You’ve probably heard the term “cyber threat” used more than once in the context of cybersecurity. What you may not know, however, is that the term “threat” is often mistakenly used to refer to other risks to cybersecurity, such as vulnerabilities. Although these three terms may seem to mean the same thing, they each have their own meaning. This fact holds true in the context of WordPress site security.
It’s more important than ever to understand the differences between threats, risks, and vulnerabilities, considering that cyberattacks are steadily rising. Between 2019 and 2020, the Internet Crime Complaint Center saw a 69% increase in cybercrime complaints owing to a rising number of ransomware attacks, a popular example of cyber threats.
So, to understand how vulnerability management tools and technologies work and how to use them, let’s cover the main differences between risks, threats, and vulnerabilities and how they relate to WordPress site security.
What are WordPress Threats?
Threats are what malicious third parties use to directly compromise and steal digital assets and bring business operations to a standstill. You can approach threats by breaking the term down into three categories:
- intentional threats
- unintentional threats
- natural threats
The first category, intentional threats, refers to well-known cyber attacks such as phishing and malware that threat actors use to target security and software systems. Unintentional threats are associated with simple human error, such as forgetting to lock the door to a business’s server room. Natural threats are just that. They are threats attributed to forces of nature such as inclement weather. While not technically related to cybersecurity, can still compromise data assets.
As we mentioned, phishing scams are some of the most popular ways threat actors try to compromise software and security systems. If you’re trying to remain vigilant against intentional threats like phishing scams, remember that bad actors often use URLs that mimic, but are not identical to, the website they’re attempting to copy.
Additionally, if you receive an email to your WordPress site that you suspect is illegitimate, simply check the signed-by domain from which the email was sent. We also highly recommend that you confirm that your WordPress site displays the lock icon next to its URL when you access it from your internet browser, which indicates that your site and its data are secure.
You can take several steps to ensure your WordPress site is more secure from threats like harmful snippets of code, phishing attacks, malware, and ransomware. Updating your WordPress platform to the latest version, creating strong passwords that are unique from the passwords you use for other websites, and using WordPress plugins that protect you against brute force attackers are some of the best methods we recommend.
Be sure to use two-factor authentication and constantly monitor your WordPress environments to shield yourself from threats, as well. And also check out this list on HubSpot that includes more than 20 tips to get your security in shape.
What are WordPress Vulnerabilities?

Vulnerabilities, unlike threats, stem from weaknesses that are present in your web design, software systems, and hardware. Whereas threats are forces that compromise and steal data assets, vulnerabilities are gaps that threat actors can take advantage of to execute their cyberattacks.
Specifically, those gaps most often take the form of network vulnerabilities, flaws in operating system policies that unintentionally provide backdoors through which viruses and malware can enter, and simple human error.
WordPress owners have several ways to spot vulnerabilities at their disposal by using vulnerability management tools and technologies.
It also doesn’t hurt to employ the help of web design professionals who can provide QA testing and ensure you’re using advanced custom web solutions such as secure logins. Web design and development professionals can also assist with localization and accessibility as well as reliability and performance analysis for your site to mitigate potential vulnerabilities.
As a WordPress administrator, one of your top priorities should be implementing security measures with the right vulnerability management tools and technologies to guard against malicious software.
Sometimes, however, your site may already be compromised without you even knowing. Fortunately, you can scan your WordPress site using tools like Sucuri to identify vulnerabilities present in your site and become aware of any security breaches that have already occurred. These tools can perform scans on your WordPress security in addition to your hosting environment and web server.
You can also choose to check your site for vulnerabilities by installing a WordPress-specific plugin like MalCare. Plugins are used to access your server in the hosting environment you’re using to execute a more thorough scan.
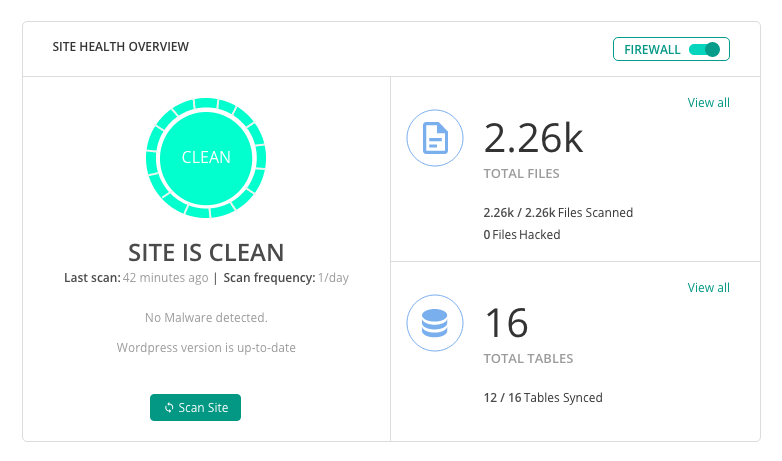
With a plugin, you can configure your scanning rules and options for automation and potentially grant access to your database if you want your plugin to scan that deeply. Ultimately, unlike scanning tools, plugins can scan your server for malicious elements that may otherwise go undetected. If you’re unsure about whether to choose a plugin or a scanning tool to detect vulnerabilities, it’s best to consult with your designed security experts to see what they recommend.
What are WordPress Risks?

Finally, we have risks, which you can think of as a combination of threats and vulnerabilities. Risks represent the potential compromise of your digital assets if a threat takes advantage of a weakness in your software, hardware, or procedures.
To keep your risk level for your WordPress site low, it’s best to:
- regularly perform plugin updates while using the latest WordPress core releases
- take regular WordPress backups of your site’s database
- use cyber risk checkup tools that perform top-level scans of your domain.
The actionable steps you need to take to mitigate risks to your site should also be repeatable ones that are part of a cybersecurity risk management plan. By including these steps in a risk management plan, you can systematically and proactively respond to risks and identify them before they occur.
Conduct a Risk Assessment

You should conduct a cybersecurity risk assessment before you develop a risk management plan:
Start by figuring out which risk areas are most at risk of being compromised. You may realize that you need to strengthen your firewalls, update your access controls, or simply institute some tried-and-true staff education on common threats like phishing and malware.
With these risk areas in mind, spend time determining how they could be compromised. Then repeat this process at least once every month. Knowing how your risk areas may be compromised allows you to anticipate potential remediation costs. Plus it gives you the opportunity to become familiar with reporting requirements that you need to fulfill in the event of a security breach.
Now, also on a monthly basis, it’s important that you review the risk assessment you’ve conducted and determine how closely it aligns with your framework for risk management. In other words, solicit regular consensus from your organization’s relevant stakeholders that your risk assessment positively contributes to your risk management framework.
If possible, designate certain personnel to assume daily or weekly responsibility for reporting risks to your WP site and other components of your IT infrastructure.
Create a Risk Management Plan
Once you’ve established a repeatable risk assessment process, it’s time to create a cybersecurity risk management plan:
The findings you’ve obtained from your risk assessment are ready for implementation into your risk management plan. You’ll need at least one security expert (though preferably a team) to conduct weekly and monthly assessments, during which your risk management process can be evaluated and improved. The stronger your cybersecurity risk management plan is, the more comfortable you (or stakeholders) will become with asking your security experts questions.
Part of your designated security experts’ responsibilities should be ingesting the research you’ve conducted and transforming it into an easily digestible risk profile. This risk profile will be a main part of what is presented to your cybersecurity risk management plan’s stakeholders, and it should lend itself to the discussions your security experts lead with other relevant employees.
These discussions should apprise employees of security best practices and the latest risks that threaten your WP site and your network.
Now that you understand the main differences between threats, vulnerabilities, and risks, you’re on the right track toward creating a plan for WordPress site security cyber risk management that you can align your WordPress site with. This risk management plan should incorporate the daily, weekly, and monthly processes that we’ve covered above, but it should also evolve based on the discussions your security experts conduct with your plan’s stakeholders.
At the end of the day, cybersecurity risks are also risks to your business operations and their continuity. Keep your business’s data and the data of your customers safe. Develop a cyber risk management plan that accounts for potential threats, vulnerabilities, and risks that can compromise the security of your WordPress site.

