Did you know that your WordPress website could be at risk of a cyber attack right now? DDoS attacks are an increasing threat to websites, causing downtime, loss of revenue, and damage to your reputation.
As a website owner, it is crucial to understand the different types of DDoS attacks and their impact on WordPress websites. It’s also vital to know how to implement effective WordPress DDoS protection to safeguard your online presence.
Table of Contents
- Understanding DDoS Attacks and Their Impact on WordPress Sites
- Essential WordPress DDoS Protection Measures
- Advanced Techniques for Enhanced WordPress DDoS Protection
- Best WordPress Security Plugins for DDoS Protection
Key Takeaways
- DDoS attacks are malicious attempts to overwhelm a server’s resources and disrupt online services.
- Different types of DDoS attacks exist. They can cause significant negative impacts on WordPress websites, leading to downtime, financial losses, customer unhappiness, and reputation damage.
- For optimal security, choose reliable hosting, implement WAFs & CDNs, monitor traffic, use geo-blocking, IP blocklisting, and strengthen WordPress with plugins.
Understanding DDoS Attacks and Their Impact on WordPress Sites
DDoS attacks are becoming increasingly common. Malicious actors seek to disrupt the normal functioning of websites by overwhelming them with traffic from multiple sources. This type of cyber attack does not provide access to a website. Instead, it sends an overwhelming number of requests to the web server, causing the website to slow down and potentially crash. For businesses relying on web traffic for income, the consequences can be severe.
Understanding the various types of DDoS attacks, their effects, and the detection methods is a crucial step in preventing WordPress DDoS attacks.
What Is a DDoS Attack?
A Distributed Denial-of-Service (DDoS) attack is a malicious attempt by multiple sources to overwhelm a server’s resources, thus preventing the server from serving legitimate user requests.
A DDoS attack is an attempt by malicious actors to disrupt online services, websites, or applications. They do this by flooding these services with huge amounts of fake traffic. Devices with inadequate security measures and users engaging in unsafe digital activities are the most vulnerable to DDoS attacks.
What Are the Different Types of DDoS Attacks?
DDoS attacks can be classified into various types based on the OSI (Open Systems Interconnection) model layers. These include:
1. Volume-Based Attacks
These are the most common type of DDoS attack. The primary objective here is to saturate the bandwidth of the targeted site. Examples include:
- UDP Floods: Attackers send a massive number of User Datagram Protocol (UDP) packets to a target to overwhelm it.
- ICMP (Ping) Flood: Attackers send a rapid succession of ping requests to a server, making it unable to process legitimate traffic.
2. Protocol Attacks
These attacks exploit vulnerabilities in the victim’s server protocol. They aim to consume server resources or intermediate communication equipment resources, such as firewalls and load balancers. Examples include:
- Ping of Death: Attackers send oversized ping packets to crash a system.
- SYN Flood: By initiating an incomplete SYN handshake process and not allowing it to conclude, attackers exhaust server capacity.
- Smurf Attack: Attackers use broadcast networks to amplify their attack, directing traffic from a large number of devices towards a target.
3. Application Layer Attacks
Targeting the application layer, these attacks are the most sophisticated and challenging to prevent since they mimic genuine traffic. These attacks exhaust the server resources, like RAM and CPU, with excessive requests, making them susceptible to a brute force attack. Examples include:
- HTTP Flood: Attackers send a series of HTTP GET or POST requests to a website, aiming to overwhelm its server.
- Slowloris: Designed to keep as many connections to the target web server open for as long as possible, eventually overloading it.
- DNS Query Flood: Attackers overwhelm the Domain Name System (DNS) servers by sending a vast number of queries.
4. Amplification Attacks
These types of attacks leverage the use of publicly accessible UDP protocols. By sending small requests with a spoofed IP address (the target’s IP), the response directed at the target is significantly amplified. Examples include:
- DNS Amplification: Attackers use misconfigured domain name servers to flood a target with DNS response traffic.
- NTP Amplification: Attackers exploit Network Time Protocol (NTP) servers to overwhelm a target with User Datagram Protocol traffic.
5. Botnets
While not a DDoS attack type per se, botnets are networks of compromised computers that attackers control. These “zombie” computers are directed to attack a target simultaneously, leading to overwhelming traffic. Botnets play a crucial role in executing high-volume DDoS attacks.
Effects of DDoS Attacks on WordPress Websites
DDoS attacks can have severe consequences for WordPress websites, including:
- Website downtime
- Rendering the site inaccessible to users
- Financial losses for businesses that rely heavily on web traffic
- Customer dissatisfaction
In addition, a successful DDoS attack can hurt a website’s reputation, potentially leading to a loss of trust among users and customers.
How to Detect a DDoS Attack on WordPress?
Detecting a DDoS attack on a WordPress site can be challenging without proper monitoring and analysis. Website owners should closely monitor site activity, watching for unusual patterns or spikes in traffic that could signal an attack. Using security tools can assist in monitoring and analyzing website traffic, helping to detect potential WordPress DDoS attacks.
Immediate action is required if you suspect your WordPress site is under a DDoS attack. Contact your hosting provider and any security service providers to help protect your website and mitigate the attack.
Essential WordPress DDoS Protection Measures
Adopting strong protection plans is vital to keep your WordPress site protected against DDoS attacks.
1. Secure Your Hosting Environment
One of the most critical aspects of WordPress DDoS protection is securing your hosting environment. Choosing a reliable hosting provider with built-in DDoS protection can significantly reduce the risk of falling victim to an attack.

A hosting provider with advanced networking hardware and robust data centers can help ensure that your website remains accessible to legitimate users. At the same time, they block malicious traffic from reaching your server.
2. Implement a Web Application Firewall (WAF)
A WAF is a security solution designed to block malicious requests and protect against DDoS attacks. By analyzing incoming traffic and blocking suspicious requests, a WAF prevents them from reaching your website’s server. This helps prevent WordPress DDoS attacks from overwhelming server resources and causing your website to crash.
3. Use a Content Delivery Network (CDN)
A Content Delivery Network (CDN) is a network of servers that can enhance website performance and provide protection against DDoS attacks. By storing website data close to visitors and distributing it across multiple servers, a CDN reduces the load on your origin server. This makes it harder for attackers to target a single server.
Using a CDN not only improves site performance but also acts as a barrier against DDoS attacks.
Advanced Techniques for Enhanced WordPress DDoS Protection
To further strengthen your WordPress site’s DDoS protection, you can consider implementing advanced techniques such as monitoring and analyzing website traffic. Additionally, consider using geo-blocking, IP blocklisting, and hardening your WordPress installation.
We will delve into these advanced techniques and discuss how they contribute to safeguarding your website from DDoS attacks.
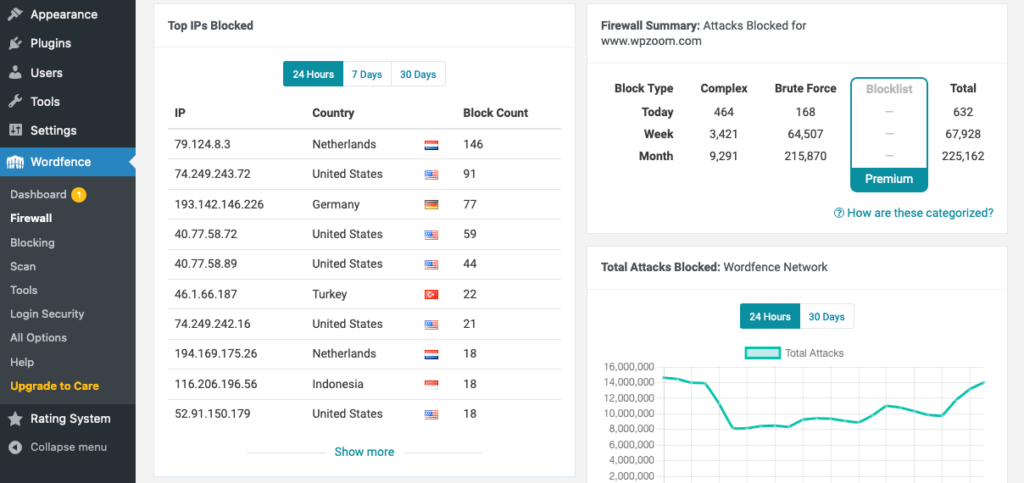
1. Monitor and Analyze Website Traffic
The monitoring and analysis of website traffic play a vital role in DDoS protection. By keeping a close eye on the activity on your website, you can detect and prevent potential attacks at an early stage.
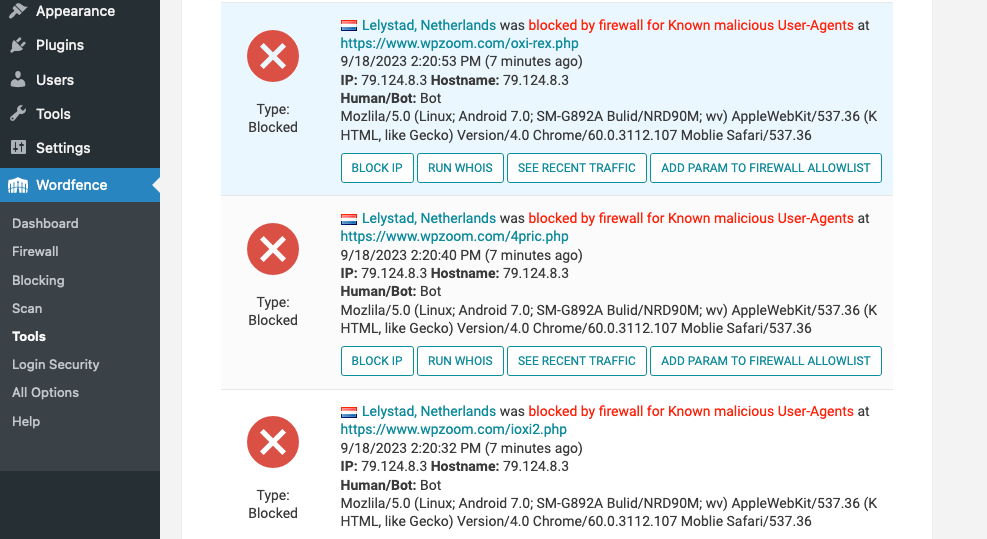
Using WordPress security plugins can help monitor and analyze website traffic. These tools provide valuable insights into potential DDoS threats and allow you to take action before an attack becomes overwhelming.
2. Implement Geo-Blocking and IP Blocklisting
Geo-blocking and IP blocklisting are advanced techniques that can help block suspicious traffic and reduce the intensity of DDoS attacks. By preventing IP addresses from specific countries from accessing your network, you can limit the potential for DDoS attacks to harm your website.
Applying these techniques via a WAF or a content delivery network (CDN) provides an added layer of defense against DDoS attacks.
3. Harden Your WordPress Installation
This involves implementing additional security measures to protect your website from potential attacks and vulnerabilities. This includes:
By hardening your WordPress installation, you can effectively reduce the risk of DDoS attacks and other security threats.
4. Disable REST API
The WordPress REST API is a feature that provides a way for developers to interact with sites remotely by sending and receiving JSON (JavaScript Object Notation) objects. Disabling the WordPress REST API can also help secure your site from potential attacks.
While it can be a powerful tool for developers, it can also be exploited by malicious actors if left unprotected. Therefore, disabling it can be an effective way to limit the potential attack surface of your site.
However, it’s important to note that some plugins and WordPress themes may rely on the WP REST API to function correctly, so always check for potential compatibility issues before disabling it.
5. Disable XML-RPC
XML-RPC is a feature in WordPress that enables data to be transmitted, with HTTP acting as the transport mechanism and XML as the encoding mechanism. Since WordPress isn’t a standalone system and occasionally needs to communicate with other systems, this was initially designed to allow for that.
However, with the advent of the WordPress REST API, the XML-RPC has become somewhat obsolete and is now commonly seen as a potential security risk. It’s because it provides a relatively easy way for hackers to execute brute force attacks. This is why it’s recommended to disable XML-RPC if you don’t need it.
However, some plugins and services still rely on XML-RPC, so it’s essential to check if any of your plugins require it before disabling it.
Best WordPress Security Plugins for DDoS Protection
In addition to the essential and advanced techniques discussed above, using the best WordPress security plugins, including anti ddos plugins, can further enhance the security of your website.
We will present an overview of the leading WordPress security plugins, highlighting their features and the advantages they bring for DDoS protection.
Wordfence Security
Wordfence Security is a popular WordPress security and anti-DDoS plugin that provides the following features:
- Firewall protection
- Two-factor authentication
- Malware scanning
- Brute force protection
By actively monitoring and preventing DDoS attacks, Wordfence Security can help protect your website from potential harm and ensure its availability to legitimate users.
Sucuri Security
Sucuri Security is a comprehensive website security and protection platform that offers a range of services, including malware cleanup, monitoring, and robust security features. In addition, it provides a WordPress plugin to help bolster the security of WordPress websites.
With features such as malware scanning and brute force attacks protection, Sucuri Security can significantly enhance your website’s DDoS protection.
iThemes Security
iThemes Security is another popular WordPress security plugin that offers a wide range of features to protect your website from various security threats, including DDoS attacks:
- Two-factor authentication
- Malware scanning
- Brute force protection
It also offers a range of additional features, such as password strength enforcement and user action logging.
FAQ
Does WordPress Have DDoS Protection?
WordPress does not offer native DDoS protection. However, third-party services and plugins can be used to enhance the security of your WordPress website and protect it against DDoS attacks.
What Is the Best DDoS Protection for WordPress?
The best DDoS protection for WordPress depends on individual needs and budget. A combination of a reliable hosting provider with built-in DDoS protection, a web application firewall (WAF), and a content delivery network (CDN) can help protect your website from DDoS attacks.
Additionally, WordPress plugins can further enhance your site’s protection.
Is it Illegal to DDoS a Website?
Yes, in most countries, DDoS attacks are illegal. However, laws and penalties can vary by jurisdiction. It’s crucial to be familiar with local regulations, but generally speaking, engaging in such attacks can lead to significant legal consequences, including fines and imprisonment. Always prioritize ethical and legal standards when operating online.
Can DDoS Attacks Be Accidental?
Accidental DDoS attacks are rare. Most DDoS attacks are intentional and malicious, carried out by attackers seeking to disrupt the normal functioning of a website or network resource.
Conclusion
In summary, DDoS attacks pose a significant threat to WordPress websites, and it is crucial for website owners to take early actions to protect their online presence. By understanding the different types of DDoS attacks and their impact, you can begin implementing essential protection measures. Additionally, considering advanced techniques will further safeguard your WordPress site from potential harm. Stay alert, stay protected, and maintain the trust of your users and customers.

