If you run a website, specifically an e-commerce website, it is your responsibility to ensure that transactions occur securely and that the data of your users and clients are not compromised. Your WordPress website’s database stores personal data, physical and electronic addresses, credit card details, transaction logs, and much more, and you are responsible for the security and integrity of all this data.
Security is not synonymous with inviolability. There is no such thing as absolute security on the Internet, especially when it comes to open-source software. However, there are many security measures that you can take to minimize risks of breaches, data theft, and other more or less serious damage to your website or infrastructure. Remember that, according to the GDPR, the Data Controller is responsible for ensuring that data processing complies with the GDPR and data protection regulations.
The data controller determines the purposes for which and the means by which personal data is processed. So, if your company/organization decides ‘why’ and ‘how’ the personal data should be processed, it is the data controller. Employees processing personal data within your organization do so to fulfill your tasks as data controller.
A security flaw in a website can put a company’s life at risk. Who would want to entrust their credit card details to an insecure website? And what damage would result to your brand’s reputation if your customers’ data were stolen and used for illicit purposes?
In short, on the same level as performance, security is a mission-critical factor for a successful e-commerce website and business. With this in mind, in this article, we have gathered a list of security measures and best practices that every e-commerce owner should adopt in order to remain competitive in local and international markets and avoid serious legal liability and damage to their online business.
13 major security risks for e-commerce websites
According to the 2020 Trustwave Global Security Report, traditional brick-and-mortar retailers and e-commerce environments are the most exposed industries to cybersecurity risks, with about 24% of the total security incidents in 2019.
This leads us to consider the importance of security for e-commerce websites, find out the threats that loom over an online business, and the measures that e-commerce site owners must take to secure their customers’ transactions and data.
To better understand the actions and best practices an online business owner must adopt to secure their websites and e-stores, we first need to understand the most dangerous threats to e-commerce websites.
Based on the OWASP Top 10 Web Application Security Risks, we compiled the following non-exhaustive list of the most widespread threats that e-commerce websites have to face today.
1. Malware and Ransomware
There are many types of malware and different levels of security threats. Hackers use them to hack devices and steal data. Malware can cause severe monetary damage and can even destroy an entire company.
Although the consequences may not always be so dire, your customers may receive the error message “The site ahead contains malware” or “Deceptive site ahead” or the like, and this can affect your site’s visibility in SERPs and damage your brand image seriously.
Ransomware is a sub-species of malware. In short, ransomware hijacks a device or website, denying access to its files until the victim pays a ransom for the decryption key.
Due to the high risk that a malware attack can have on an e-commerce website, scanning your e-commerce site regularly for malware infections is vital for your business.
Check Out Our Video Guide to Malware
2. Phishing
Phishing is a kind of social engineering attack used by cybercriminals to spread malware — usually through emails.
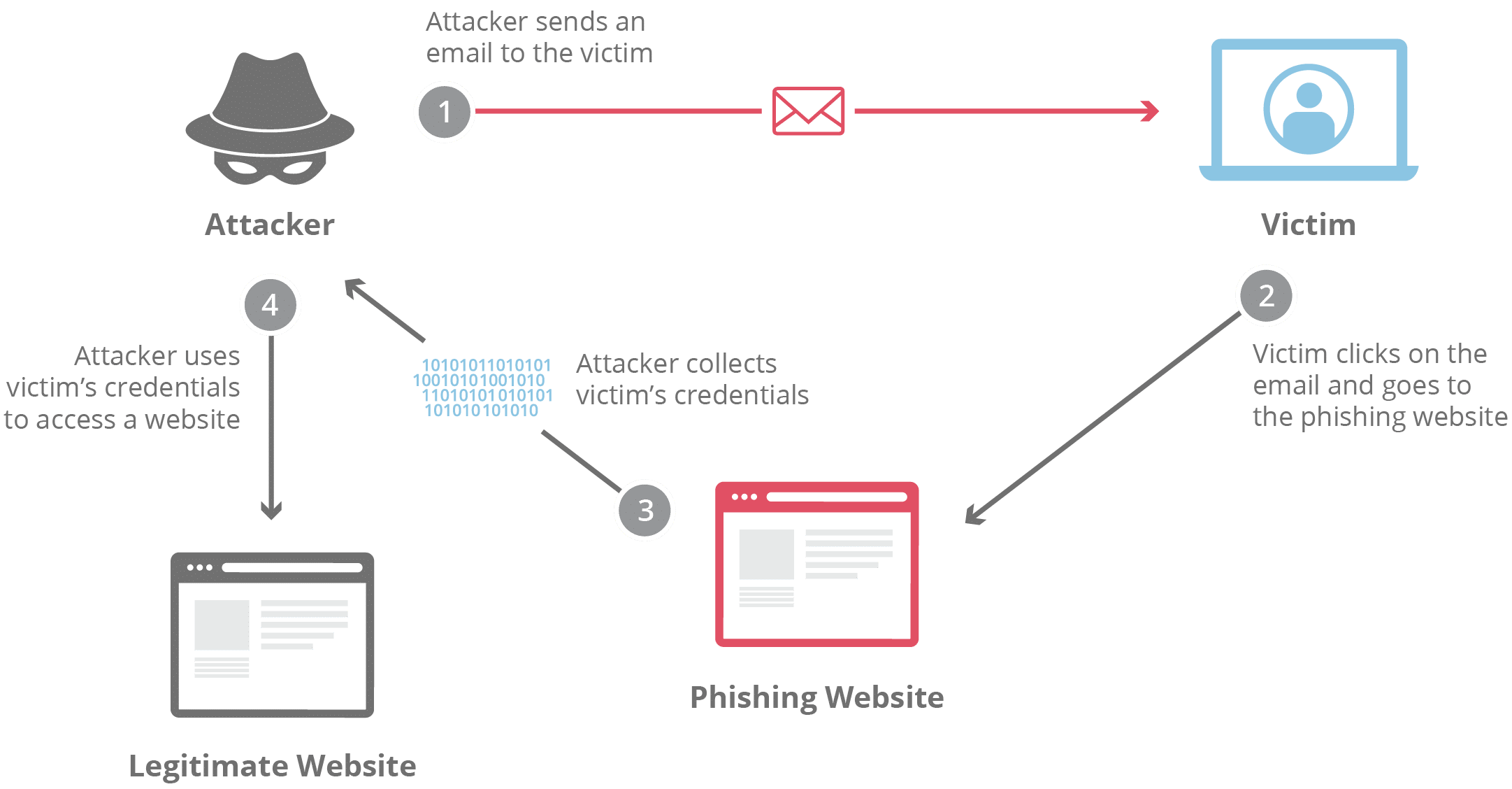
It refers to an attempt to steal sensitive information such as usernames, passwords, credit card or bank account details, or other important data to use or sell with malicious intent. Typically, this type of attack is carried through spam and other forms of fraud emails or instant messages.
3. DDoS attacks
DDoS is the short term for distributed denial of service. This is a type of attack that floods a website with a large number of requests to overwhelm the server with excessive Internet traffic and take the website down. The consequence is that your site goes offline, and the bandwidth costs increase dramatically. This can also cause the suspension of your hosting account.
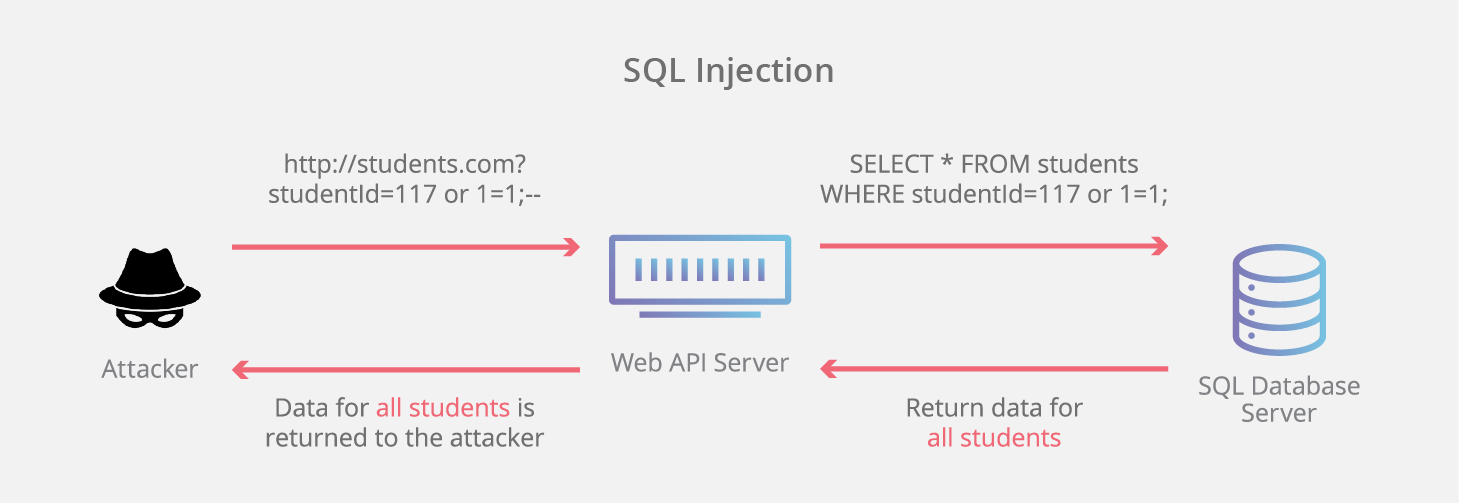
4. SQL injection
SQL injection is a kind of attack performed by a malicious actor who tries to inject SQL statements into a web application. If the attack is successful, they’ll be able to access your site database and read, modify, or remove data.
5. Cross-site scripting
Cross-Site Scripting (XSS) is a kind of attack where someone attaches malicious code onto a website to be executed on page load. The injection happens on a user’s browser and typically aims to steal sensitive information.
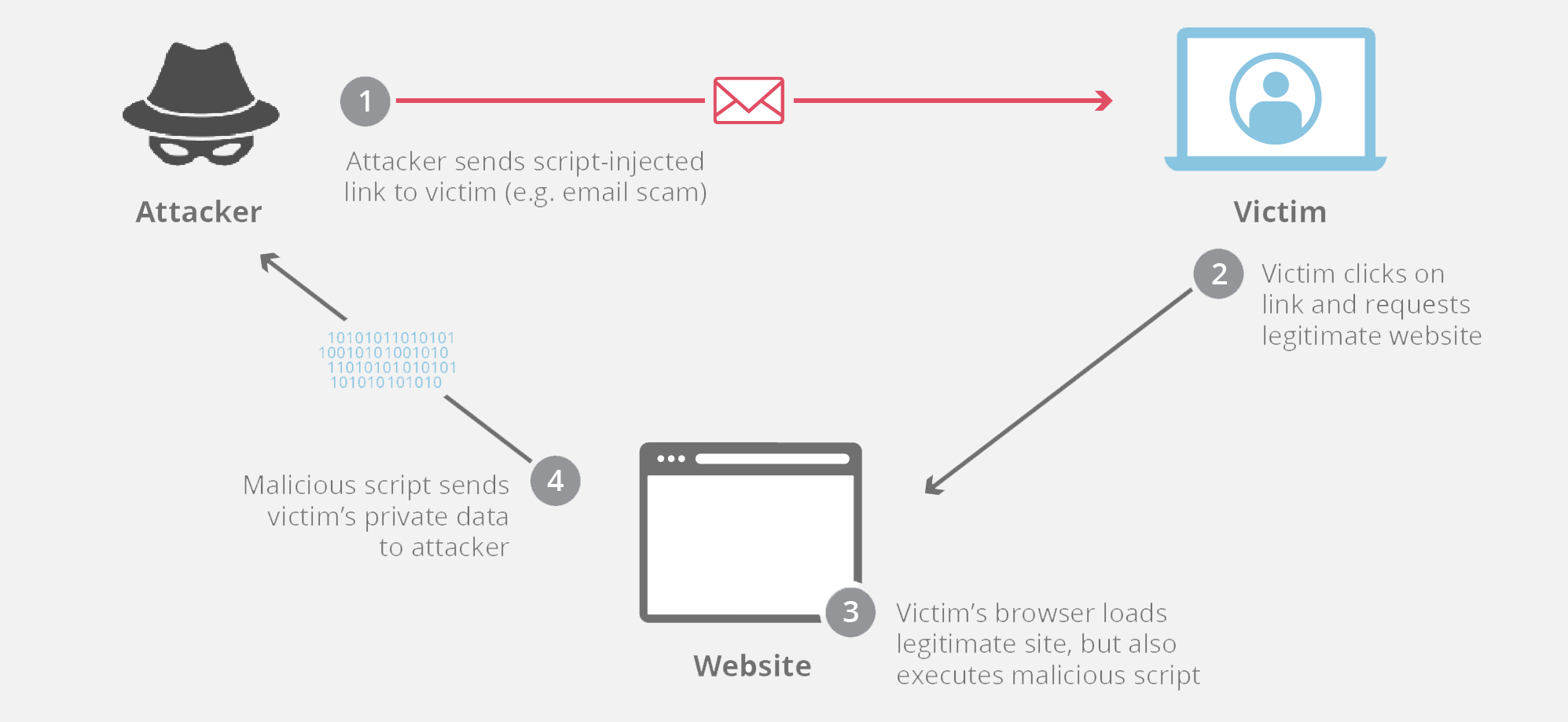
6. Man-in-the-middle attacks
A man-in-the-middle (MitM) or on-path attack is a cyberattack where someone places in the middle of communication between two devices (such as a web browser and a web server) aiming to grab information and/or impersonate one of the two agents with malicious intent.
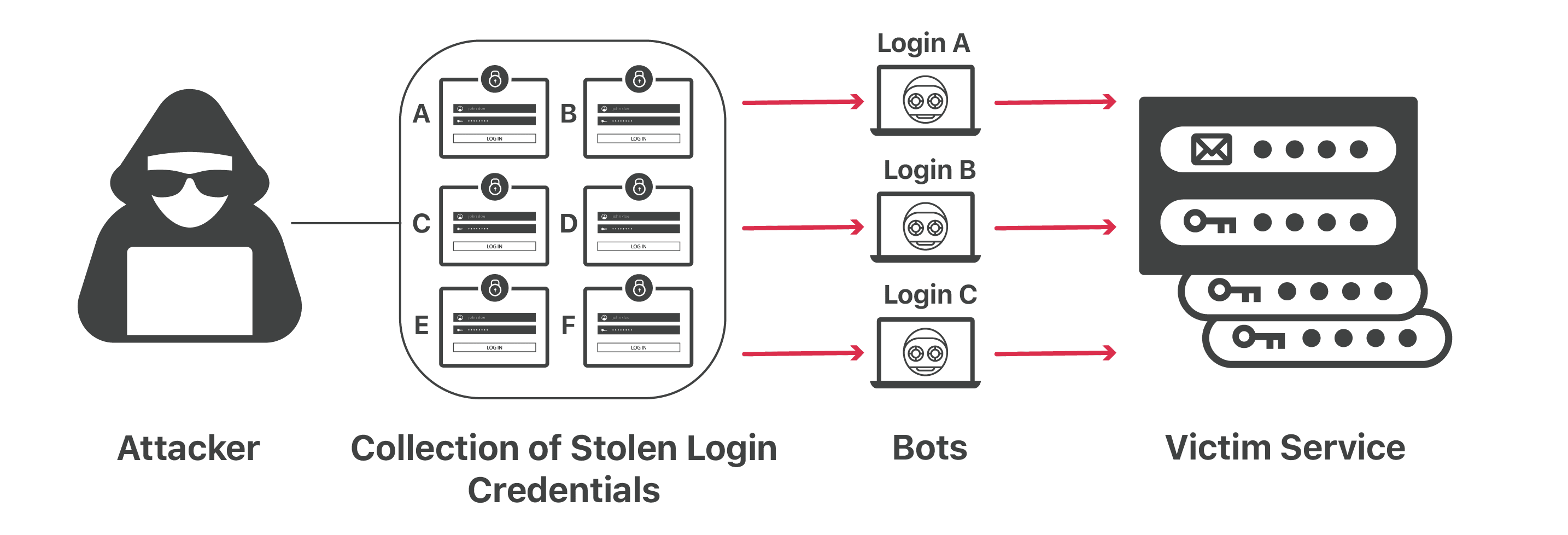
7. Credential stuffing
Credential Stuffing is a cyberattack where the attacker uses credentials obtained from a data breach on a service or website to log into a different service or website. This kind of attack is a common risk for professionals working from home and remote companies.
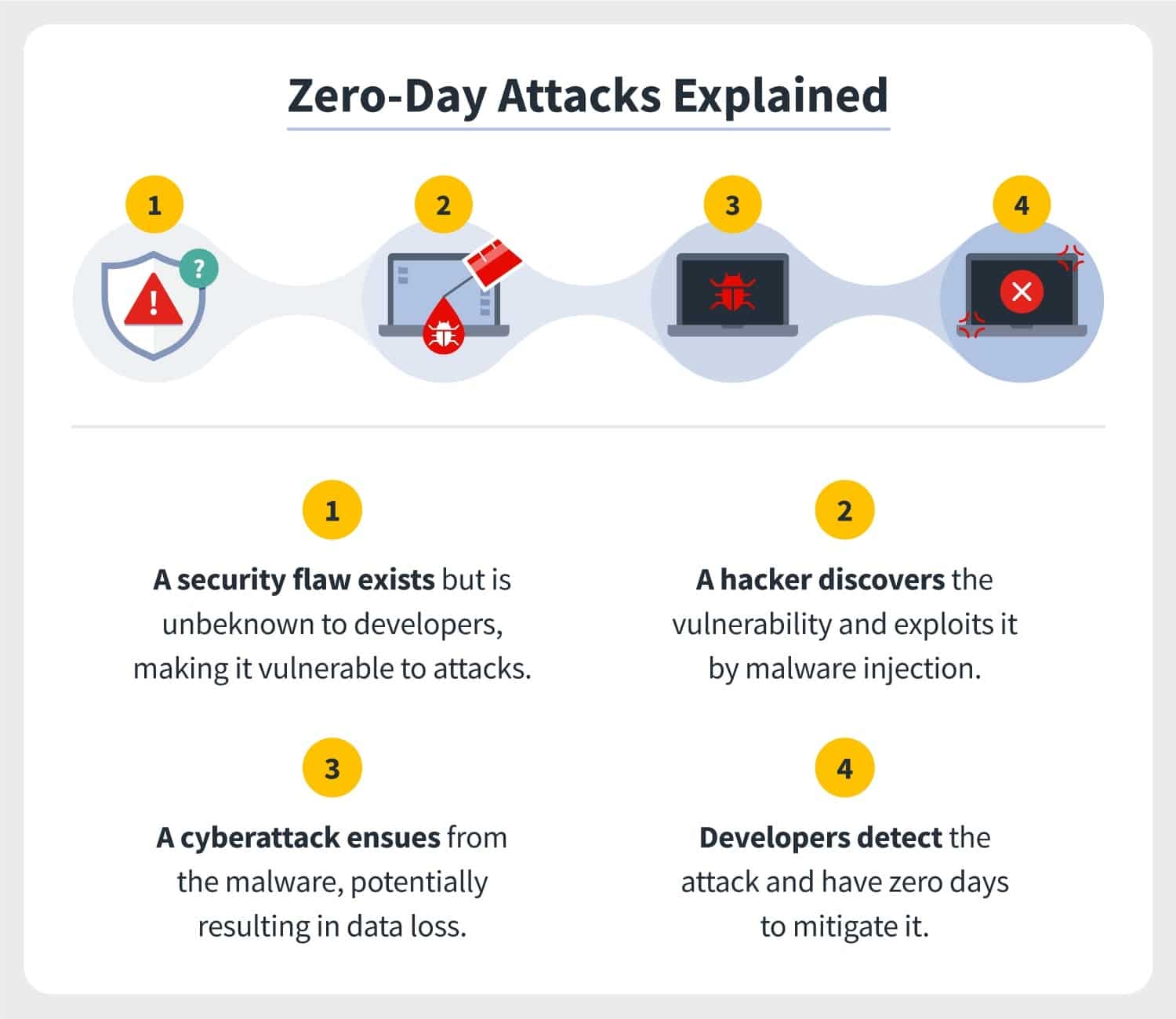
8. Zero-day exploits
A zero-day exploit is an unresolved or previously unknown security vulnerability that has no fix in place. Zero-day means that you have zero days to fix the issue before it causes serious damage to your business.
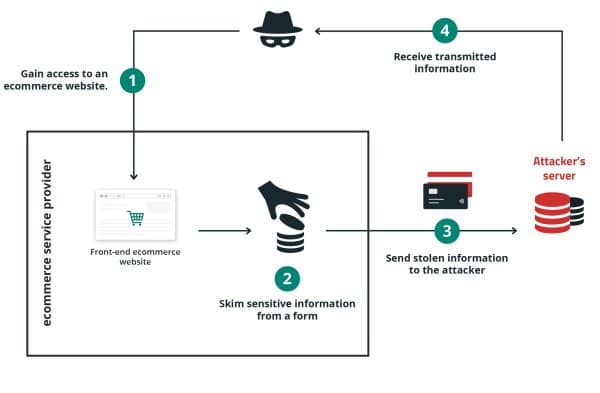
9. E-skimming
E-skimming or digital skimming is the insertion of malicious software into a retailer’s website aiming to steal payment data during checkout. This is also known as Magecart attack.
10. Brute force attacks
A brute force attack is a trial-and-error method used to decode sensitive data such as login credentials, API keys, and SSH credentials. Once a password has been compromised, it can be used to access other services if you use the same credentials on multiple websites. (See credential stuffing.)
Using strong passwords, enabling multi-factor authentication systems, and using a robust password manager are all best practices preventing this kind of cyberattacks.
11. Backdoors
A backdoor provides a way to bypass an authentication or encryption system to automatically log into a website, device, or service. Once a website or service has been breached, a malicious actor can create their own backdoors to access your website, steal data, and potentially destroy your entire site.
12. Social Engineering attacks
Social engineering attacks are particularly dangerous because they exploit characteristics of human nature: trust in others, lack of knowledge, discomfort in contravening an order, utilitarianism, and so on. The basis of social engineering is the psychological manipulation of people for the purpose of disclosure of confidential information such as passwords, bank account details, and financial information.
The most common channels used to perform this kind of attack are emails, chat, phone calls, social networks, websites, and others. The attacker can then use that information to conduct other kinds of exploits such as Cross-Site Request Forgery.
Check Out Our Video Guide To Understand All About CSRF Attacks
13. Supply Chain Attacks
Typically, with a supply chain attack, a cyber attacker infiltrates malicious code into a vendor’s software to be distributed with an update.
Although they are not as widespread as other backdoor attacks, supply chain attacks have been recently detected on several WordPress plugins.
9 best practices to secure your e-commerce website
Securing a website can be a tough task if you don’t have the right tools and skills, but it doesn’t have to be a job for dedicated engineers. The main thing is to be aware of the areas of vulnerability and educate yourself and your team on the best practices for securing your e-commerce website from the most common threats.
Your task is twofold: on the one hand, you are responsible for securing WordPress and WooCommerce, determine who can access the platform, the plugins to be installed, the payment gateway, the authentication system, and everything related to WordPress, plugin, and theme maintenance. On the other hand, you need a secure and cutting-edge infrastructure. This is where the quality of your web hosting service comes in.
Sure, your web hosting provider cannot save you from any kind of threats. There are security actions that you and only you, as a site owner, can take. But a secure hosting service that takes your site’s security seriously can help a lot. Here are the main security-related features to look for in a modern web hosting service.
1. Choose a cutting-edge hosting infrastructure
The choice of the hosting infrastructure is vital to your website security, your brand reputation, and, eventually, the success of your business. You have several types of service to choose from, and they differ considerably in terms of infrastructure and services provided:
- Shared hosting
- Dedicated hosting
- VPS hosting
- Cloud hosting
- Managed WordPress hosting
For an e-commerce website, relying on a secure infrastructure is crucial. If you care about your business, a shared hosting is not an option for you as it may not guarantee the minimum security standards for a successful e-commerce website.
Dedicated hosting can be highly customized and optimized for security but may require SysAdmin skills that may be hard to find for a small or medium-sized business.
In case you need control over your hosting but you don’t have great technical knowledge and/or resources, you may opt for a Virtual Private Server (VPS) hosting, which places somewhere in the middle between shared hosting and dedicated hosting. But a VPS may have a few cons: It could be unable to handle high traffic levels or spikes and performance is still affected by other websites on the server.
A cloud hosting service may be a good option for you as it typically has several security measures in place to secure your websites. However, it can be hard to configure and manage if you don’t have the necessary skills.
A managed WordPress and WooCommerce hosting gives you peace of mind because you are not responsible for server configuration and optimization, and you have specialized support service and simplified site installation and maintenance.
A cloud-based managed WordPress hosting service merges the advantages of both worlds, combining the high-speed and secure infrastructure of cloud services with the ease of use of managed WordPress hosting services.
Kinsta hosting infrastructure and technical stack
At Kinsta, we believe we have created the fastest and most secure managed WordPress hosting solution available today on top of the Google Cloud Platform.
We provide C3D and C2 compute-optimized VMs on all plans, from Starter to Enterprise and beyond, in the regions where they are available. We also take advantage of Google secure infrastructure, which includes an enterprise-level firewall to filter out malicious traffic before it hits your website.
In addition, we have built a fast and secure technical stack based on Nginx, MariaDB, PHP 8.3, LXD containers, and our integration of Cloudflare Enterprise, which provides additional security, including a firewall, DDoS protection, and much more. This stack is available for all our clients, regardless of their plans.
We use Linux containers (LXC) and LXD to orchestrate them on top of the Google Cloud Platform (GCP), ensuring complete isolation for each individual WordPress site. On Kinsta, your website doesn’t share resources with any other website, including other websites on your account.
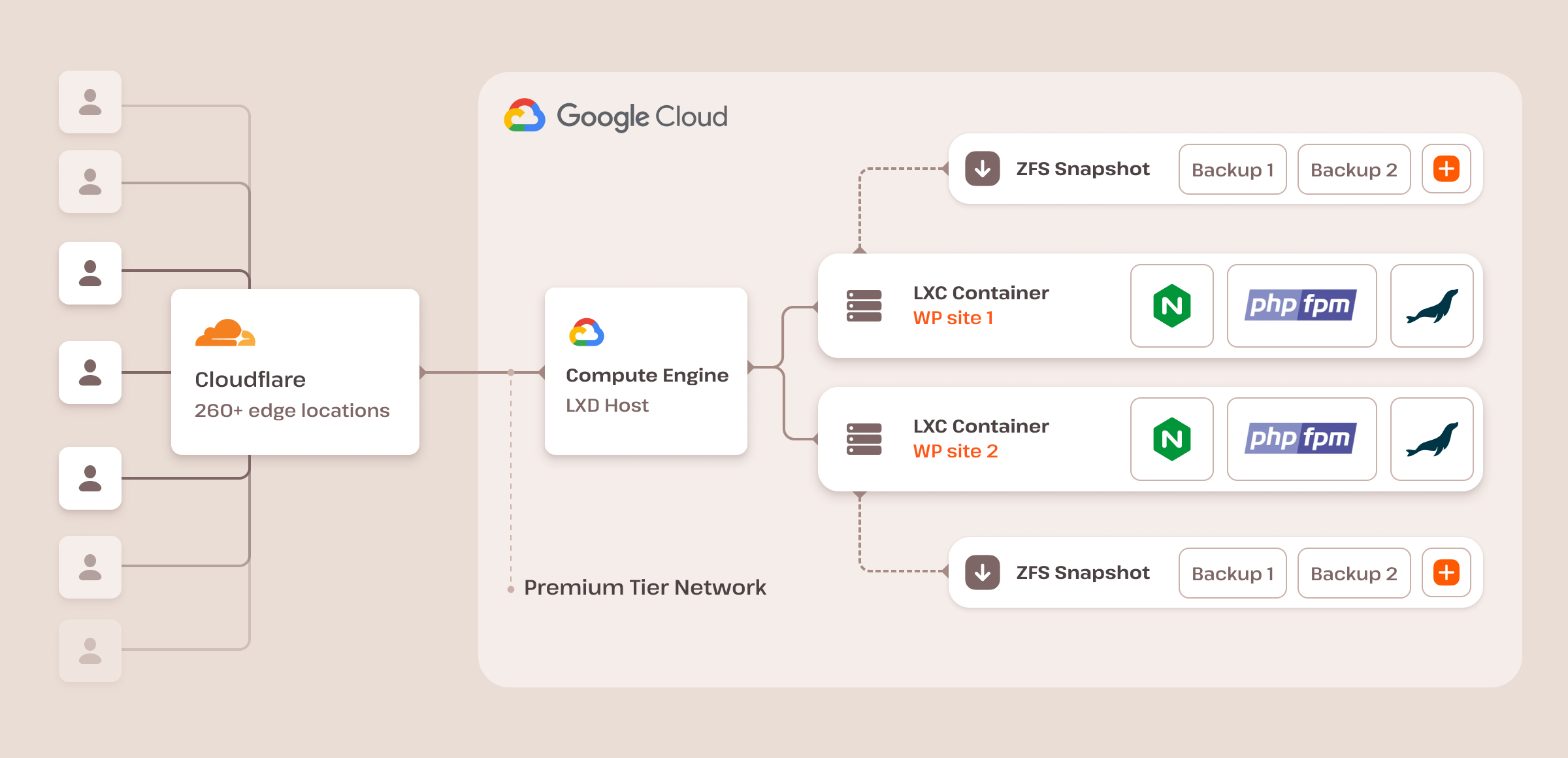
Check out this post to learn more about our cutting-edge isolated container technology.
2. Use a web application firewall
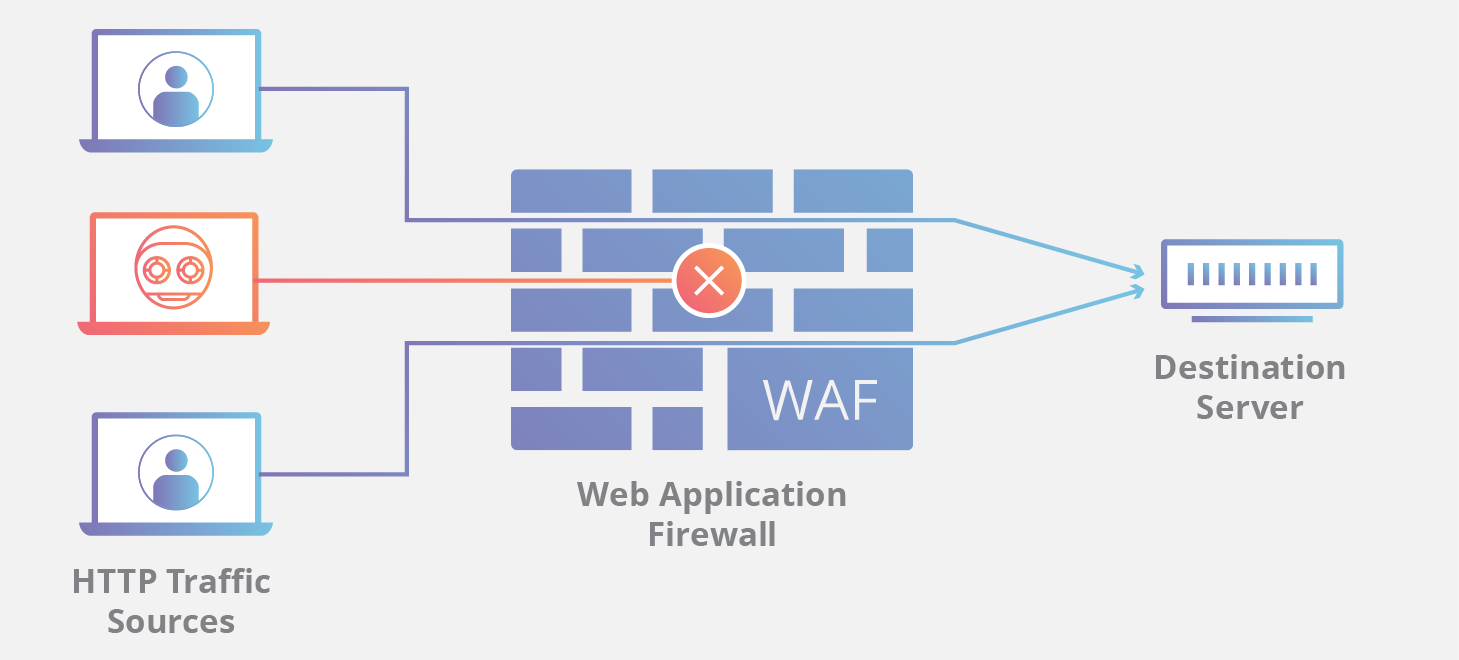
A web application firewall (WAF) is a shield that filters out malicious connections from reaching your website and keeps your WordPress website secure.
Direct connection between two computers on the Internet, such as your computer and a web server, is not secure if you don’t put a firewall in the middle. A malicious actor may infect your website with some kind of malware or launch a DDoS attack.
This is where a web application firewall comes in. It scans every single connection request to your website and blocks potentially malicious access attempts.
A WAF is crucial for your website, whether you are a first-time blogger or a successful entrepreneur. With e-commerce websites, using a web application firewall is vital because an unprotected website is an easy catch for hackers and other malicious actors.
Without a web application firewall, a hacker can easily take control of your site, change login credentials, steal or destroy data, ruin it, and perform any sort of illicit activities. Potentially, it could wipe out your site entirely. In addition, your website would be more vulnerable to DDoS and brute force attacks.
To protect your website with a WAF, you don’t need to install and configure additional software on your server. Several cloud-based options, such as Cloudflare, Sucuri, and WordFence, can be set up on your server in few minutes.
All websites hosted by Kinsta are protected by Cloudflare
In addition to the IP-based protection that we provide with the Google Cloud Platform firewall, all websites hosted by Kinsta benefit from our Cloudflare integration, which includes an enterprise-level web application firewall with custom rulesets and free DDoS protection.
Thanks to our Cloudflare integration, you don’t need to set up a WAF manually because your site is automatically secured behind Cloudflare’s firewall, regardless of the plan you subscribe to.
3. Install an SSL certificate
SSL is a protocol used to encrypt and authenticate the data sent between a client application and a web server. If you run an e-commerce website, an SSL certificate is vital for your website and your business because it ensures data encryption, website authentication, data integrity, and user trust.
In addition, an SSL certificate improves search engine ranking because search engines prefer SSL-encrypted sites. If you want to have a chance to be listed on Google’s first page, you need a valid SSL certificate with HTTPS encryption.
SSL certificates on Kinsta
If your website is hosted by Kinsta, you don’t need to deal with all the technical intricacies that an SSL typically requires. Our clients can take advantage of our Cloudflare integration, which includes automatic SLL certificates for all WordPress websites. This includes wildcard SSL certificates, which means that your SSL also covers any subdomains relating to your main domain. And if you already have one, you can also install your custom SSL certificate.
Cloudflare SSL certificates come at no cost for all our clients, regardless of their plan.
For a closer view of Kinsta WordPress SSL certificates, check out our online docs.
Check Out Our Video Guide to Choosing the Right SSL Certificate for Your Site
4. Use secure SFTP and SSH connections
To perform a manual backup of your WordPress website or manually upload a plugin or theme, you need to access the site’s filesystem via an FTP client. An FTP client typically supports both FTP and SFTP connections, but you should only rely on SFTP, that uses a secure channel to transfer files over SSH. This makes a big difference with standard FTP connections.
Kinsta only supports SFTP/SSH connections
Because SFTP is a more secure method, Kinsta only supports SFTP connections.
SFTP/SSH details are available in your MyKinsta dashboard under WordPress Sites > Sitename > Environment > Info.
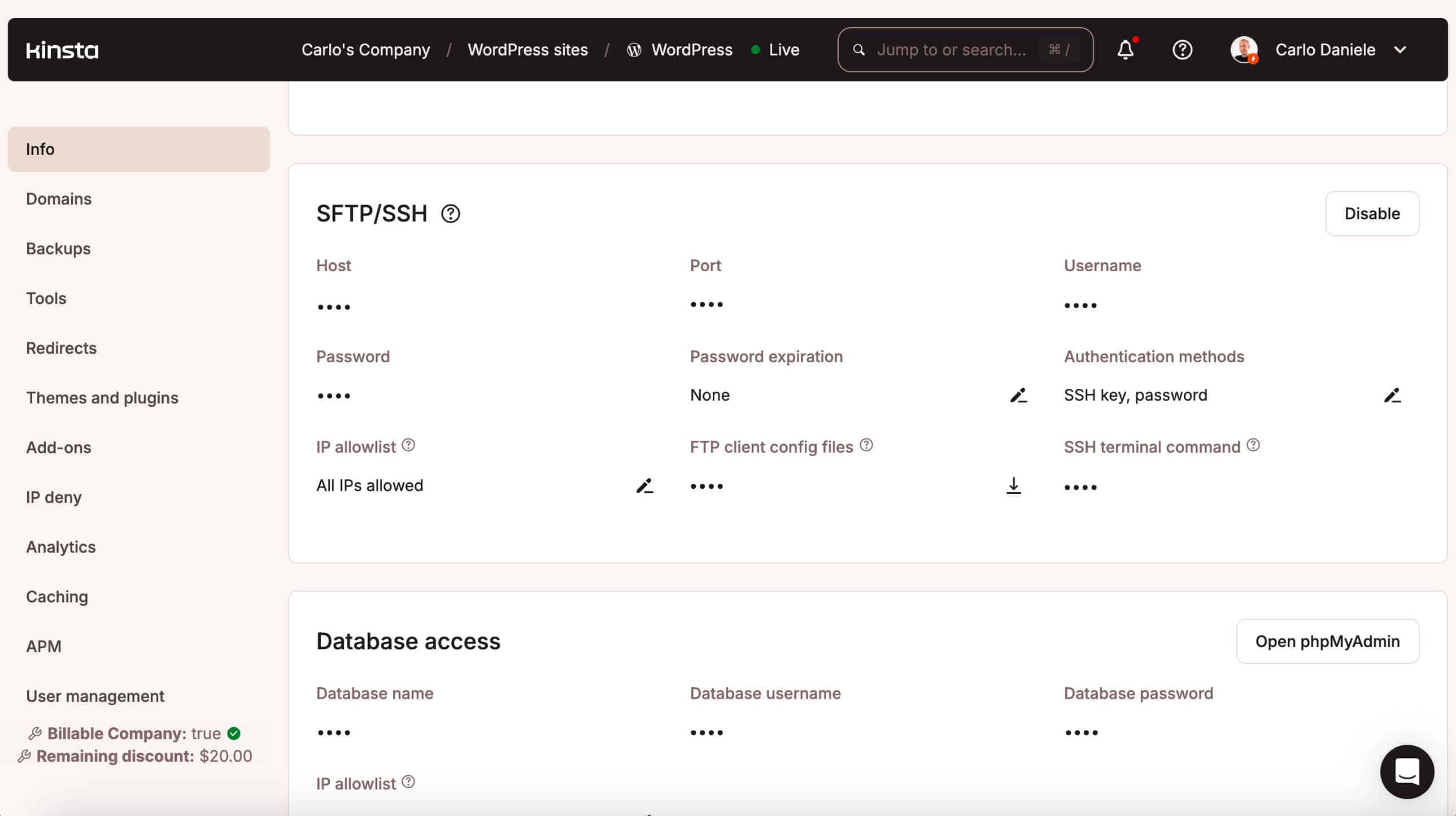
You should never use identical login credentials across multiple services and website environments. For this reason, on Kinsta, each single website environment – staging or production – has unique database and SFTP/SSH access credentials.
5. Use supported versions of PHP
Each PHP version is typically supported for two years. Only supported versions receive performance and security updates, so using unsupported PHP versions reduces performance and increases the risk of security vulnerabilities.
As of August 2024, the officially supported versions of PHP are PHP 8.1, 8.2, and 8.3.
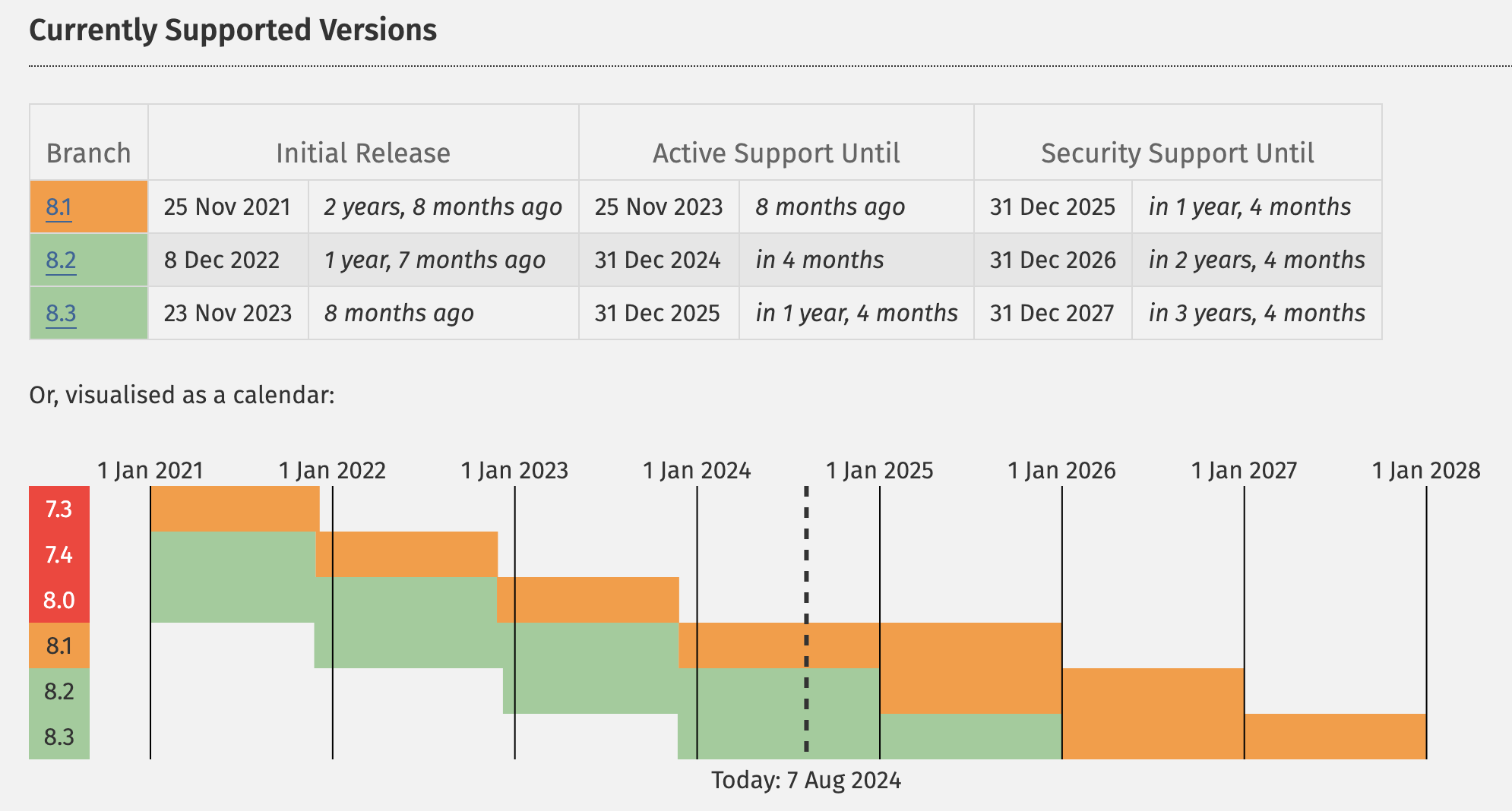
At the time of this writing, all PHP versions prior to 8.1 don’t receive security updates. This means that if you are using PHP 8.0 or earlier, your site is exposed to security flaws that will not be fixed.
WordPress core is built with PHP. Plugins are also based on PHP, and WooCommerce is no exception. If your e-commerce is based on WordPress, using a supported PHP version is vital to the success of your online store.
In addition to improved security, the most recent versions of PHP offer better performance. You could gain a boost in site speed by simply upgrading to the latest PHP version.
Kinsta only allows supported PHP versions
This may require additional development effort if you use custom plugins that are not compatible with supported PHP versions. However, our main responsibility is to ensure maximum security for your websites and our entire infrastructure. For this reason, Kinsta does not allow you to use unsupported PHP versions.
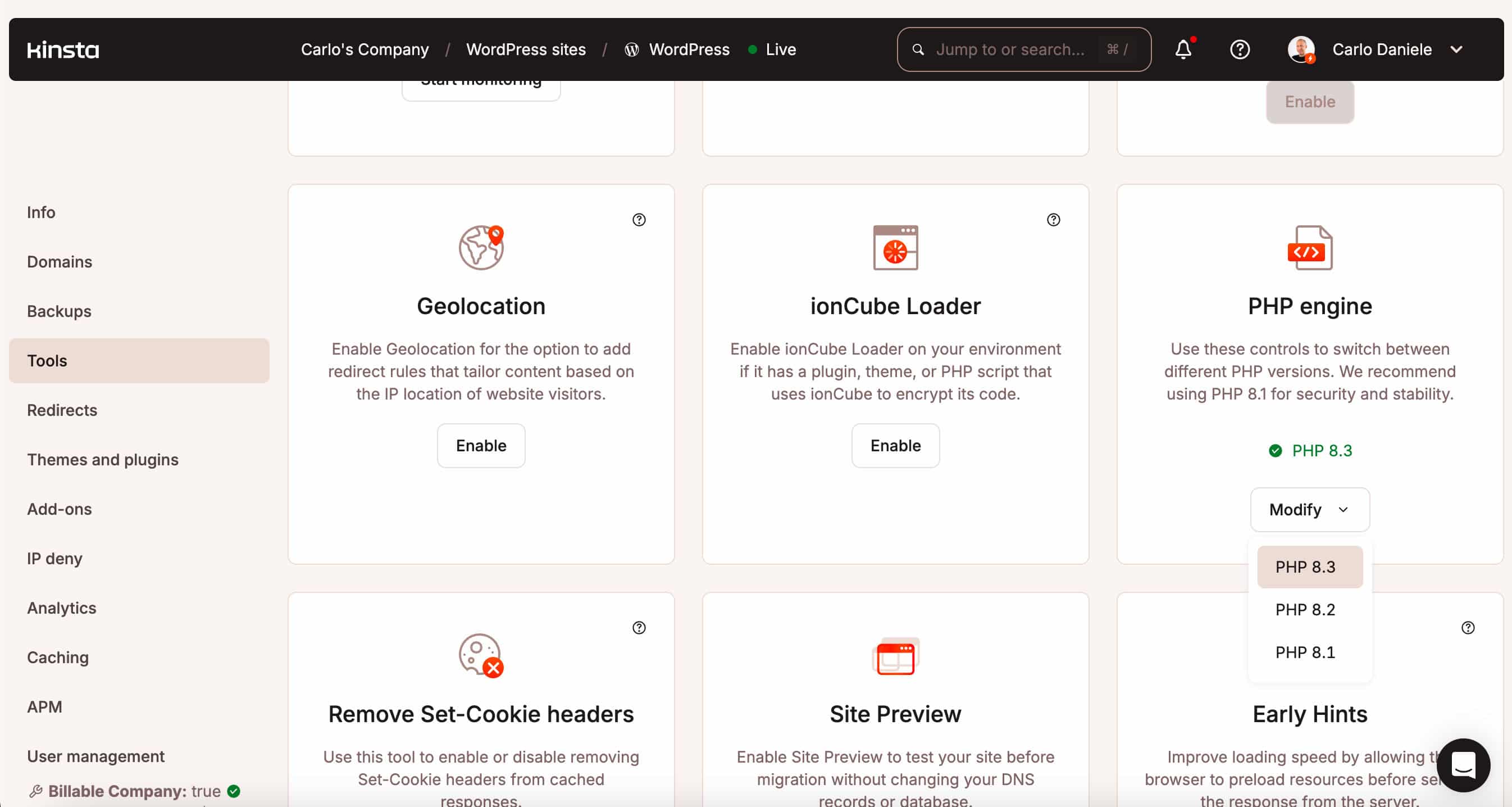
Kinsta clients can change the PHP version of their WordPress website in MyKinsta. Navigate to your site config section and select Tools from the left menu. Scroll down the page and find PHP engine. Click on the Modify button and select the PHP version for your website.
6. Enable two-factor authentication
Using strong passwords to secure your website and hosting account may not be enough to secure your e-commerce website. Using a multi-factor authentication system is strongly recommended.
Multi-factor authentication is an authentication system where the user accessing the service is required to give two or more proofs of their identity. This can be done in different ways: Biometrics such as fingerprints, an authenticator app, an email, an SMS, a hardware token, and more.
When it comes to your e-commerce website, you should enforce authentication security by enabling two-factor authentication (2FA) on both your hosting service and your WordPress website.
Enable 2FA with Kinsta
In addition to using a strong password for MyKinsta, we recommend enabling two-factor authentication and asking all users in your company to do the same. With 2FA enabled, all MyKinsta login attempts will require an additional verification code from an authenticator app (e.g., Google Authenticator) on your phone or password management app.
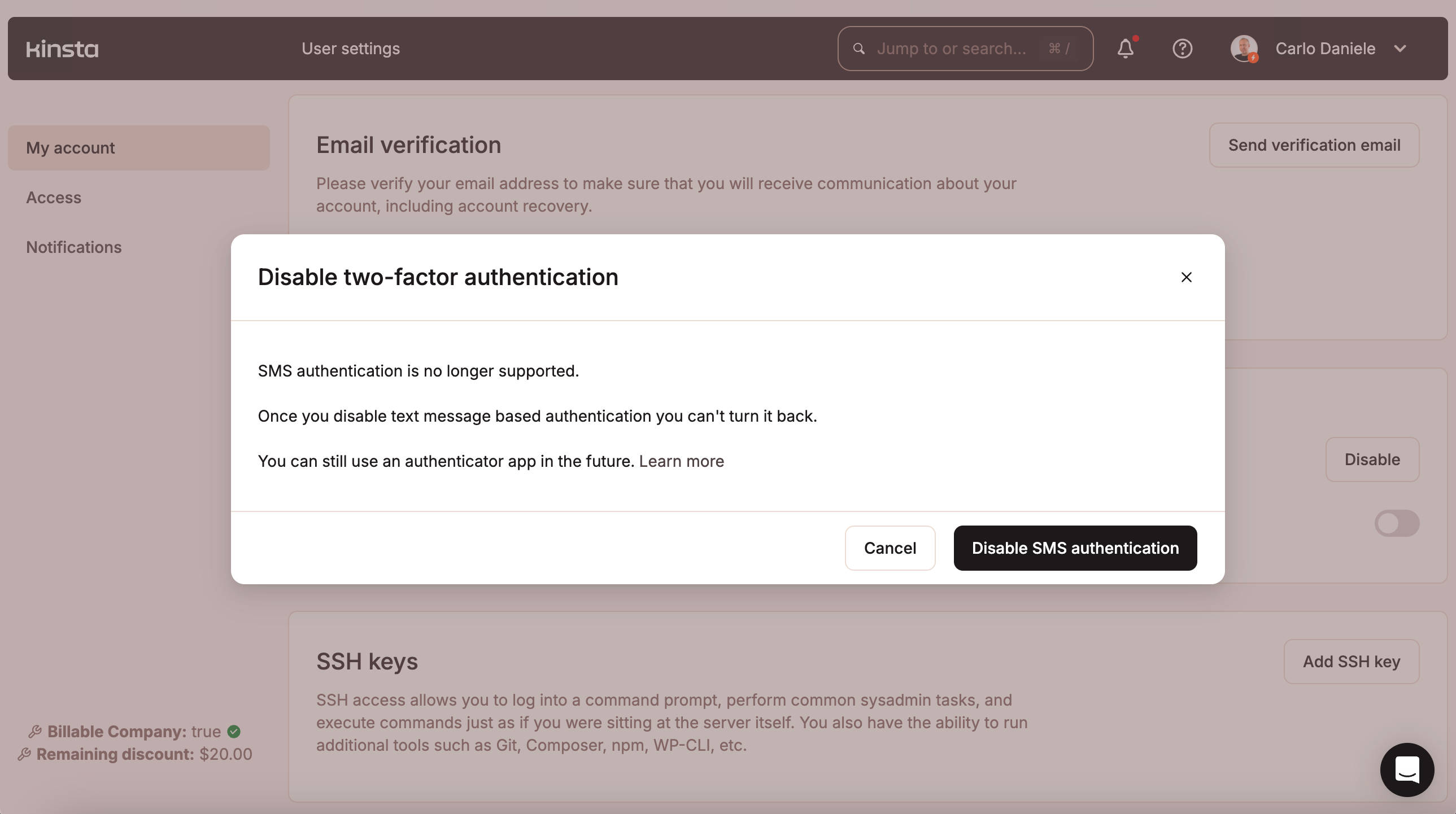
To enable 2FA in MyKinsta, click on your name in the top right corner and select User settings. In My Account, scroll the page down to the section Two-factor authentication. Click on the toggle button and scan the QR code in your authenticator app, enter the 6-digit code you see in the app, and you are done.

Note that Kinsta no longer supports SMS-based 2FA because it is vulnerable to phone-based attacks and is less secure than a time-based token. A recent Authy data breach exposed 33 million customer phone numbers, increasing the threat of SMS phishing and SIM-swapping attacks.
You can read more about 2FA on Kinsta in our documentation.
Enable 2FA with WordPress
You may also want to enable two-factor authentication on your e-commerce website. WordPress does not support 2FA out of the box, but you can quickly and easily add this feature to your website with one of the following plugins:
7. Core, plugins, and theme updates
In addition to WordPress core releases, new security updates are issued regularly whenever a new vulnerability is detected. The same happens with themes and plugins.
To keep your WordPress website protected, you need to keep your whole WordPress website up to date to prevent security vulnerabilities.
In your WordPress dashboard, under Dashboard > Updates, you can enable automatic core updates for all WordPress versions, or for maintenance and security releases only.
You can also manage automatic updates for themes and plugins.
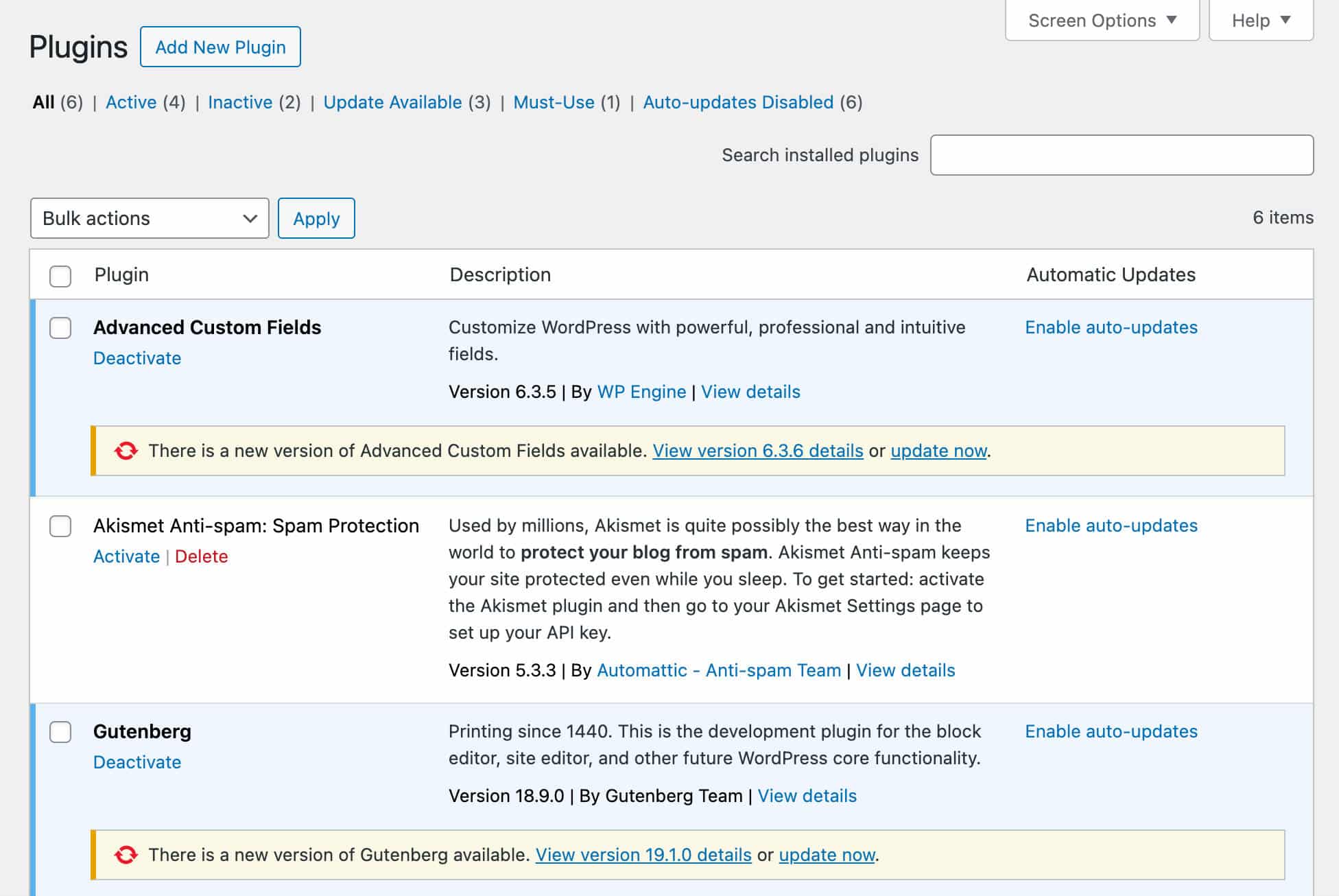
Note that, starting with WordPress 6.6, you can rollback automatic updates for your plugins in case of failure.
If you prefer, you can disable this feature and perform the updates yourself, but updating a large number of sites can be a time-consuming and boring task. That’s why many agencies resort to third-party tools that allow them to manage updates to all their WordPress sites from a single external environment.
Kinsta customers do not need to pay for third-party services to manage their updates in bulk because they can take advantage of the bulk updates feature available in the MyKinsta dashboard.
WordPress updates with Kinsta
You can manage your WordPress website themes and plugins directly from MyKinsta. In your dashboard, navigate to WordPress sites > Sitename > Themes and plugins. Here, you can select one or more plugins or themes and update them individually or in bulk.
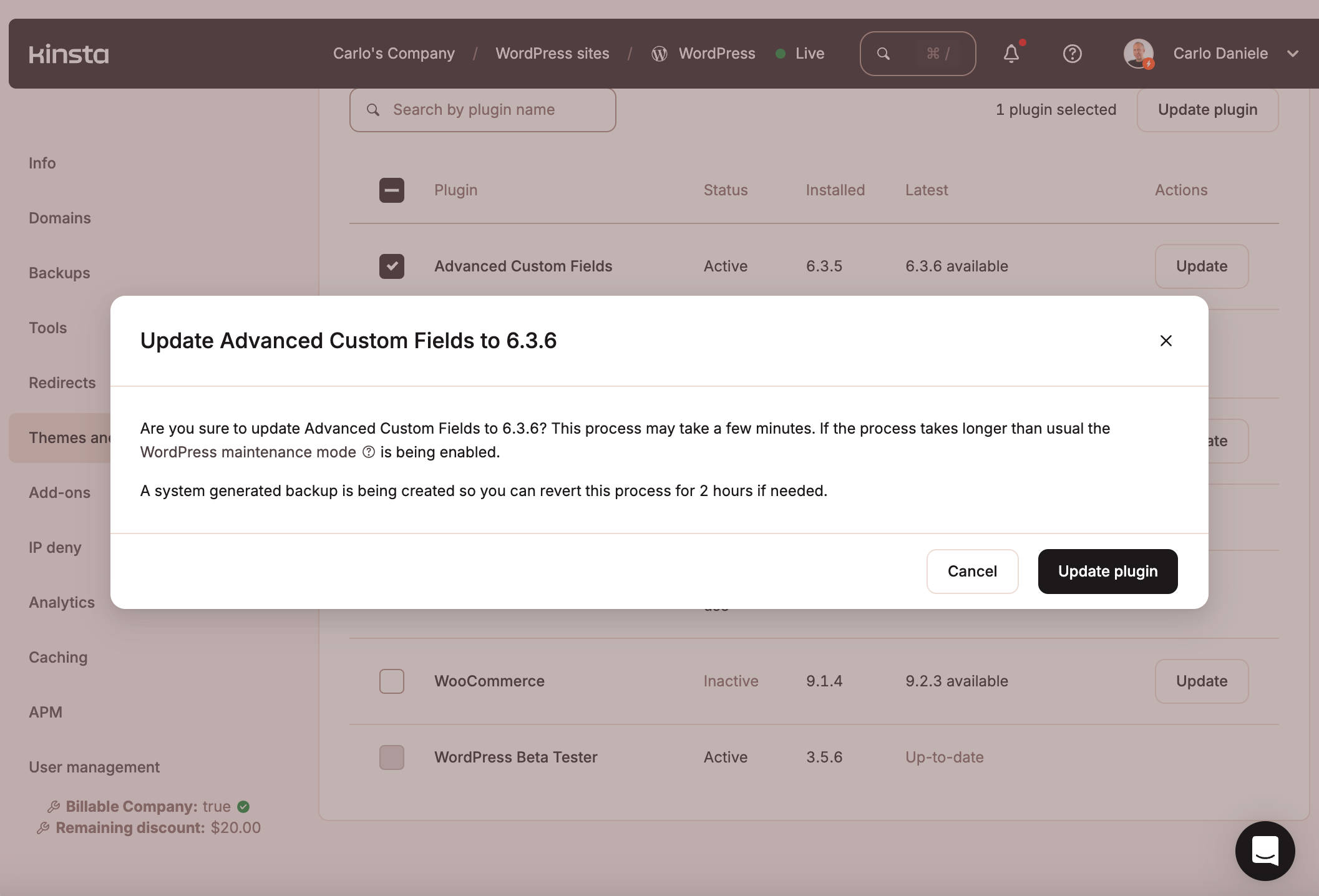
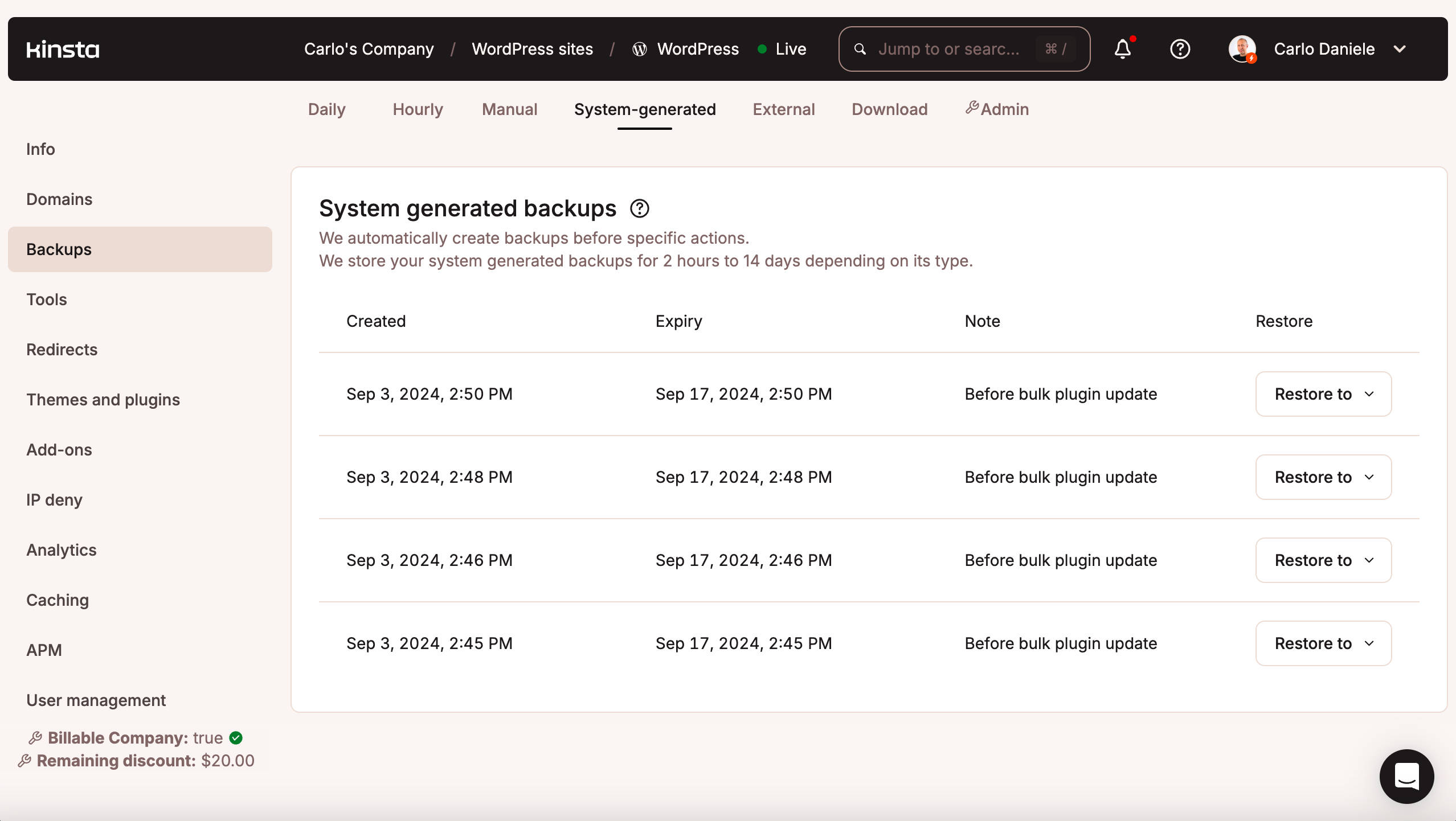
Note that when you run an update from MyKinsta, a system-generated backup is created so you can revert the process for 2 hours if the update fails. This adds a layer of security and gives you peace of mind when you need to update your plugins or themes.
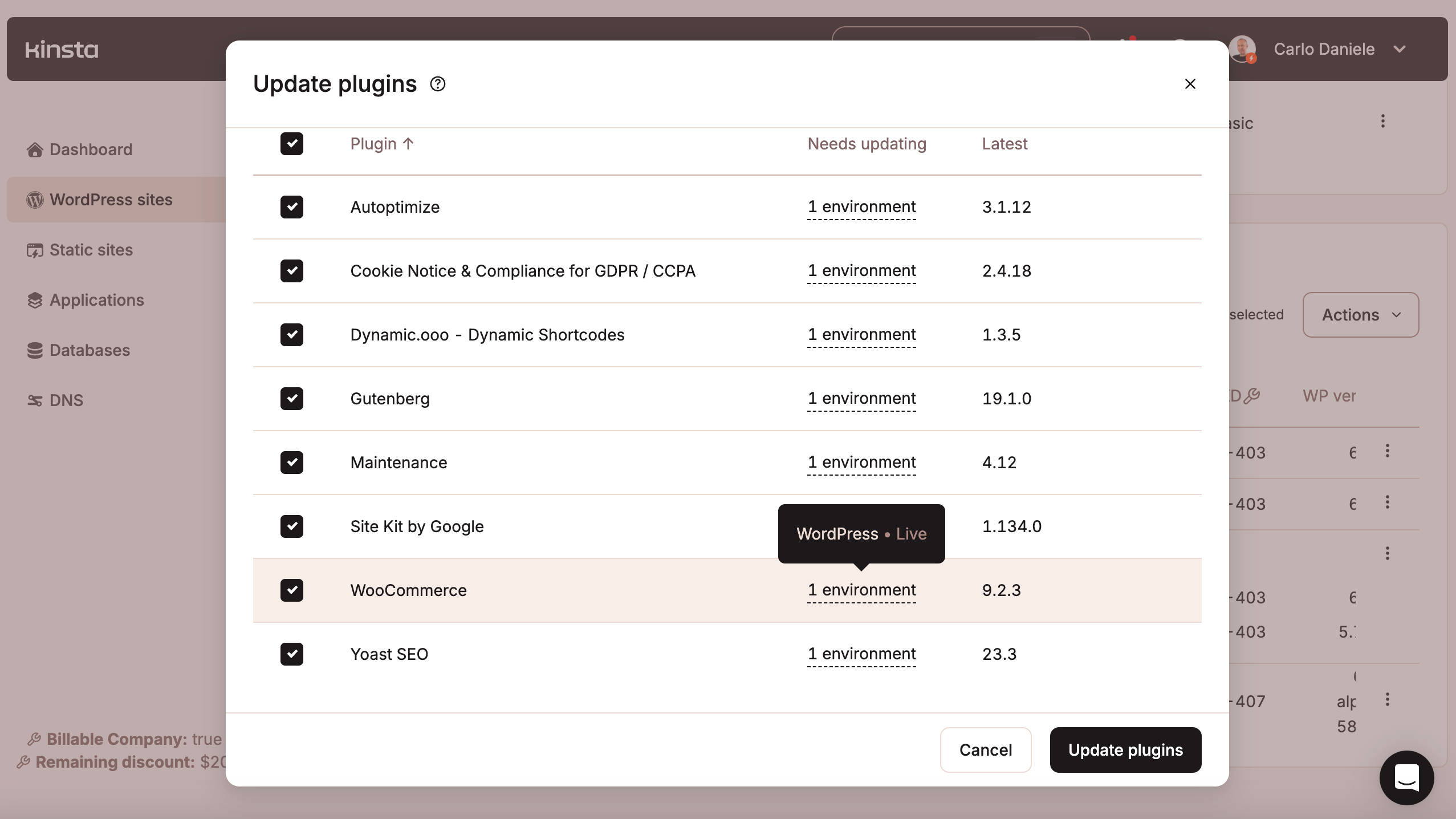
You can also run bulk updates for multiple WordPress websites at once. In your MyKinsta dashboard, select WordPress sites. Once there, select one or more websites and click on the Actions button on the right, then select the bulk action you want to perform. If you are updating plugins, click on the corresponding menu item. A pop-up will display a list of plugins for which an update is available.
Pick the plugins to update and wait a few seconds. A pop-up will let you know if the process has been completed successfully.
If the update fails, navigate to Sitename > Backups > System-generated page in MyKinsta and restore the most recent backup.
And, what’s even more powerful, you can perform all these operations on a staging environment first, then push staging to live without any risk.
On Kinsta, you can bulk update themes and plugins for all your WordPress sites conveniently from a single page without any risk. Perfect for agencies handling a lot of sites in one place.
8. Backups
If an update goes wrong, or a site is compromised or completely wiped out due to a security vulnerability, a backup can save your life. If your host does not provide an automatic backup system, you can always resort to a WordPress plugin. We recommend using a WordPress plugin that provides incremental backups: This allows you to have a backup of your site without losing disk space or reducing site performance.
However, a web hosting service that really cares about your e-commerce website should provide regular WordPress backups. Kinsta provides six different types of backup.
The six types of backups provided by Kinsta
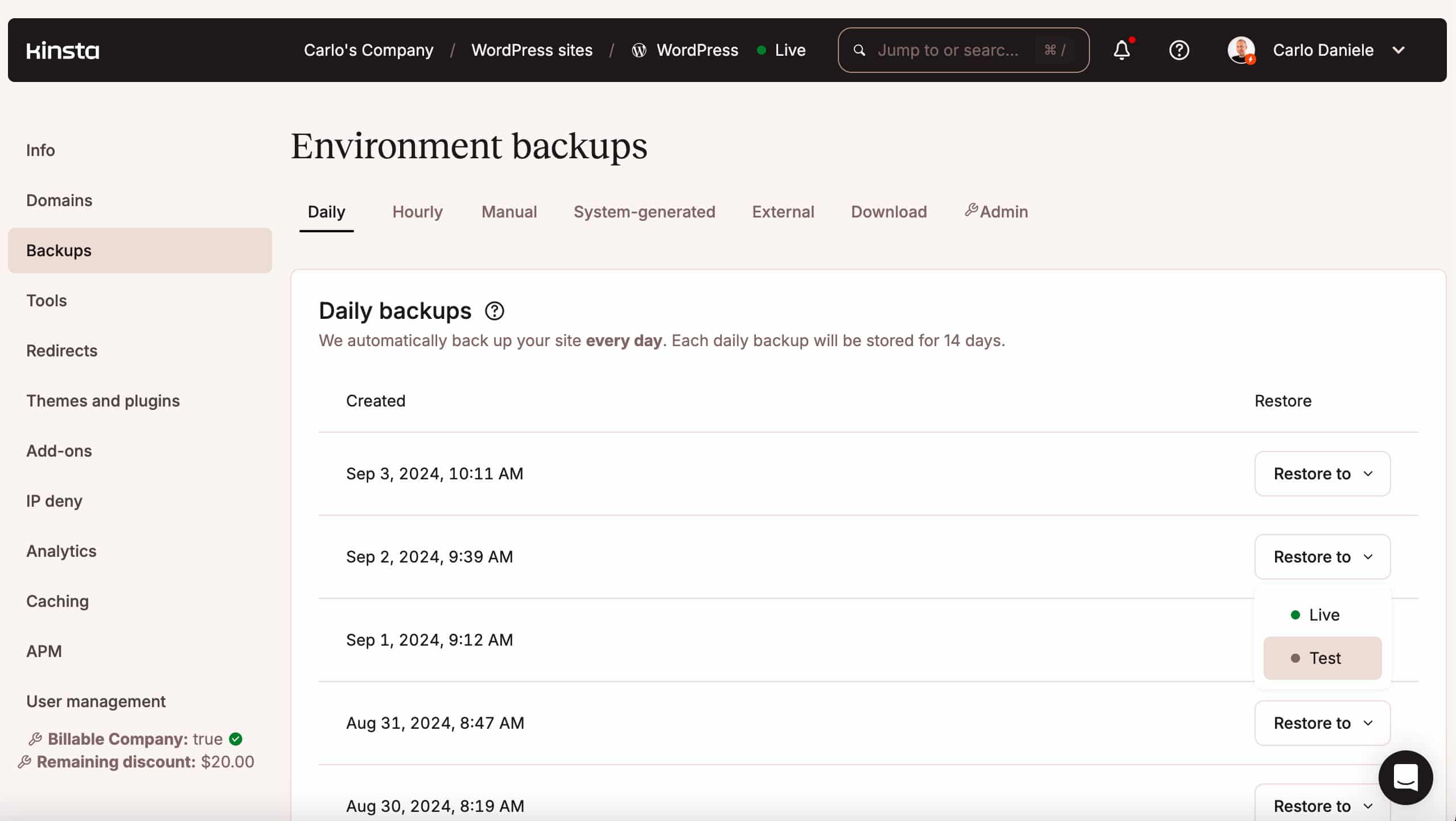
We provide daily automatic WordPress backups, as well as system-generated backups for all WordPress websites. These backups, along with manual backups, are available as restore points in MyKinsta. You can also manually create a downloadable backup once a week.
You can browse your backups in your MyKinsta dashboard under WordPress sites > Sitename > Backups. Here you can restore your backup to an environment of your choice with a single click.
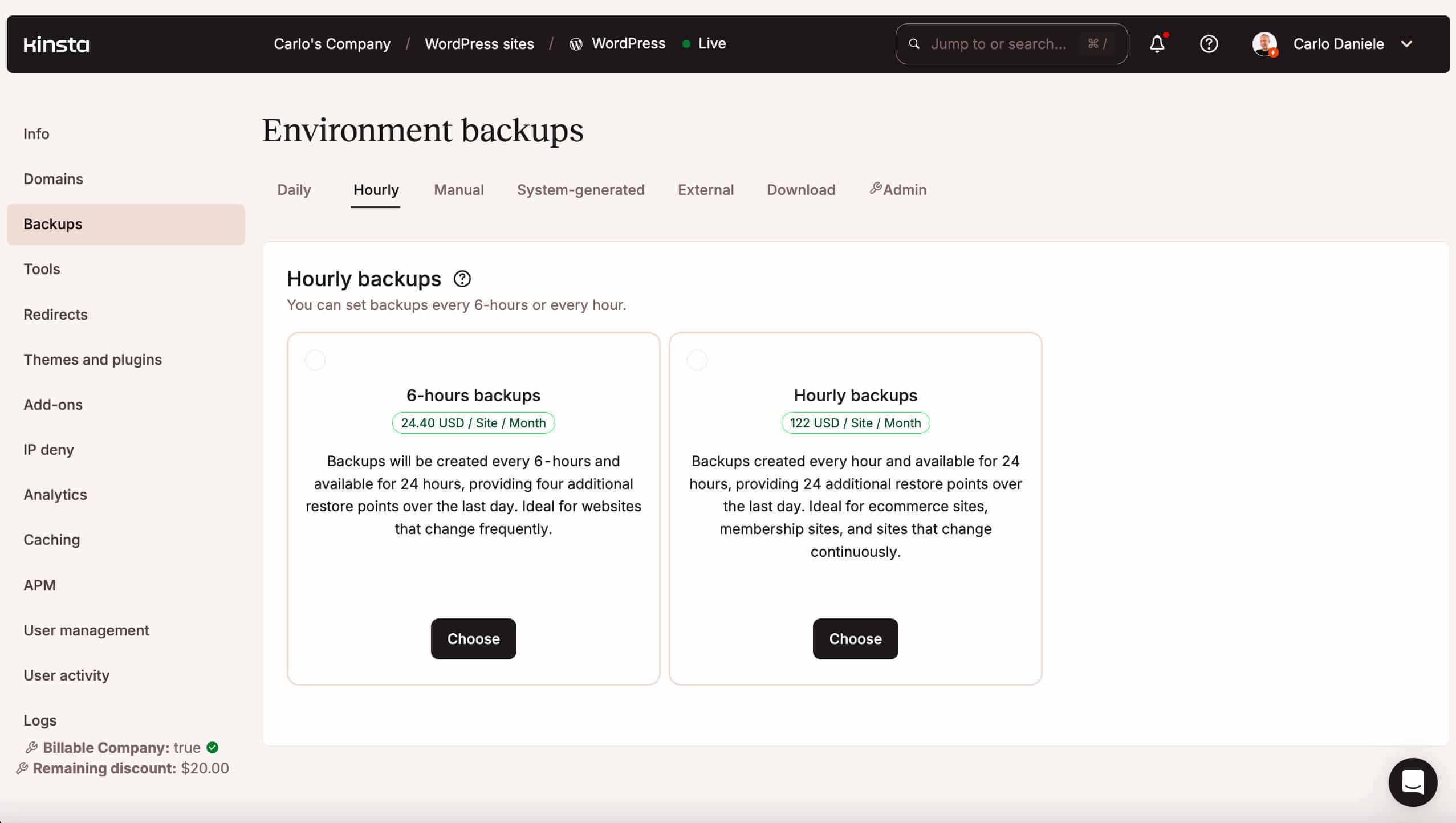
If you update your e-commerce website several times a day and you need more backups, you can purchase an add-on for hourly backups.
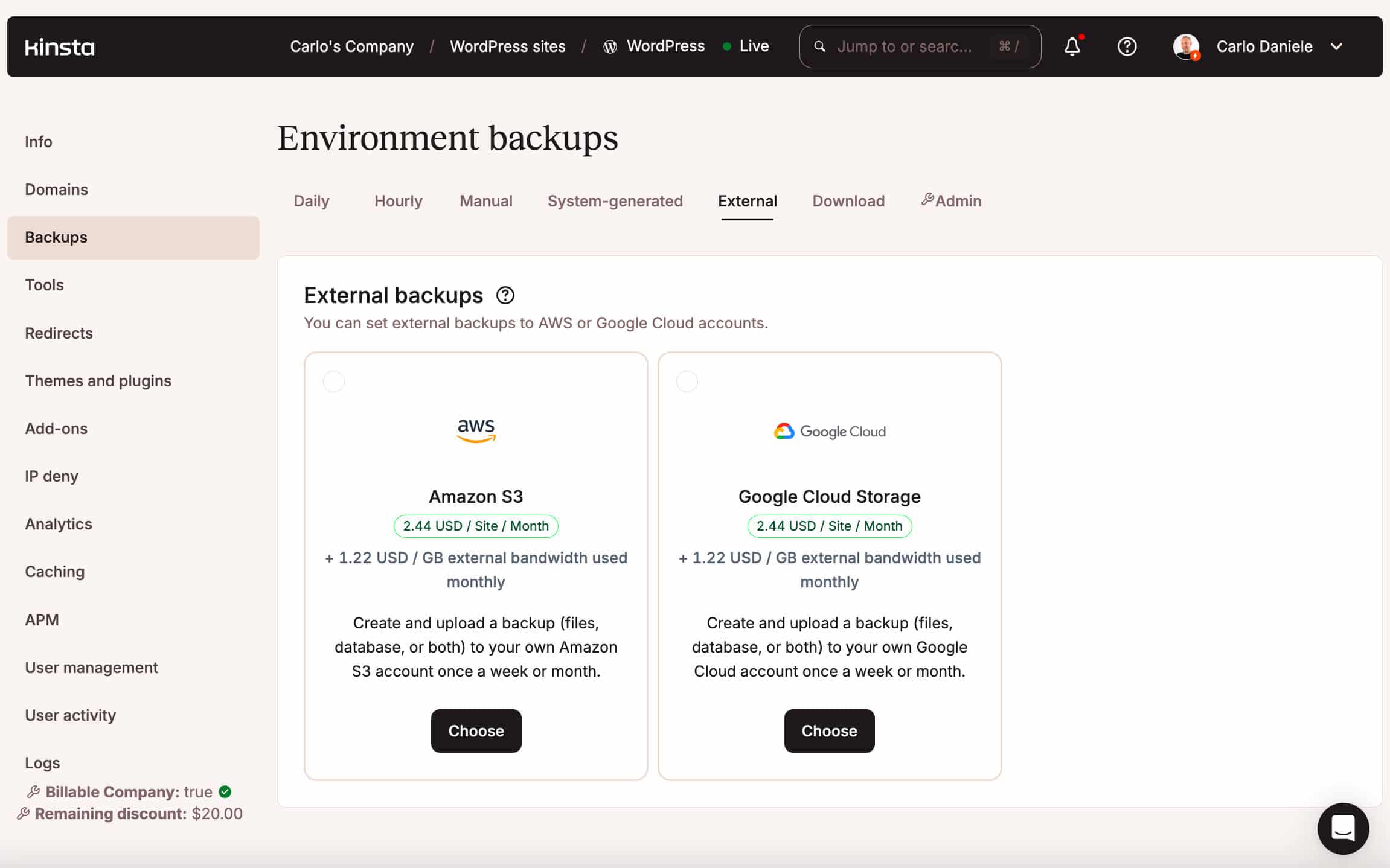
An add-on for external backups is also available, allowing you to store your backups on an external storage service such as Amazon S3 or Google Cloud Storage.
The retention period for backups is 14 to 30 days, depending on the hosting plan you subscribed to.
You can read more about WordPress backups in our docs.
9. Be careful with plugins
You often need many plugins on your WordPress website. This is especially true for e-commerce, which often requires features not available in WordPress or WooCommerce out of the box. We have a long list of recommended plugins you can browse through to see for yourself:
But you should never install the first plugin that pops up. There are some best practices to follow when choosing plugins for your WooCommerce website:
Do not install nulled plugins. This is vital for an e-commerce business. Nulled plugins are premium WordPress plugins or themes that have been hacked and can contain modified code designed to cause harm or collect information.
Prefer plugins that receive regular updates from vendors with good reputations. Trust the community and check reviews and ratings from other users. Avoid, if possible, plugins with low ratings and maintained by unknown vendors.
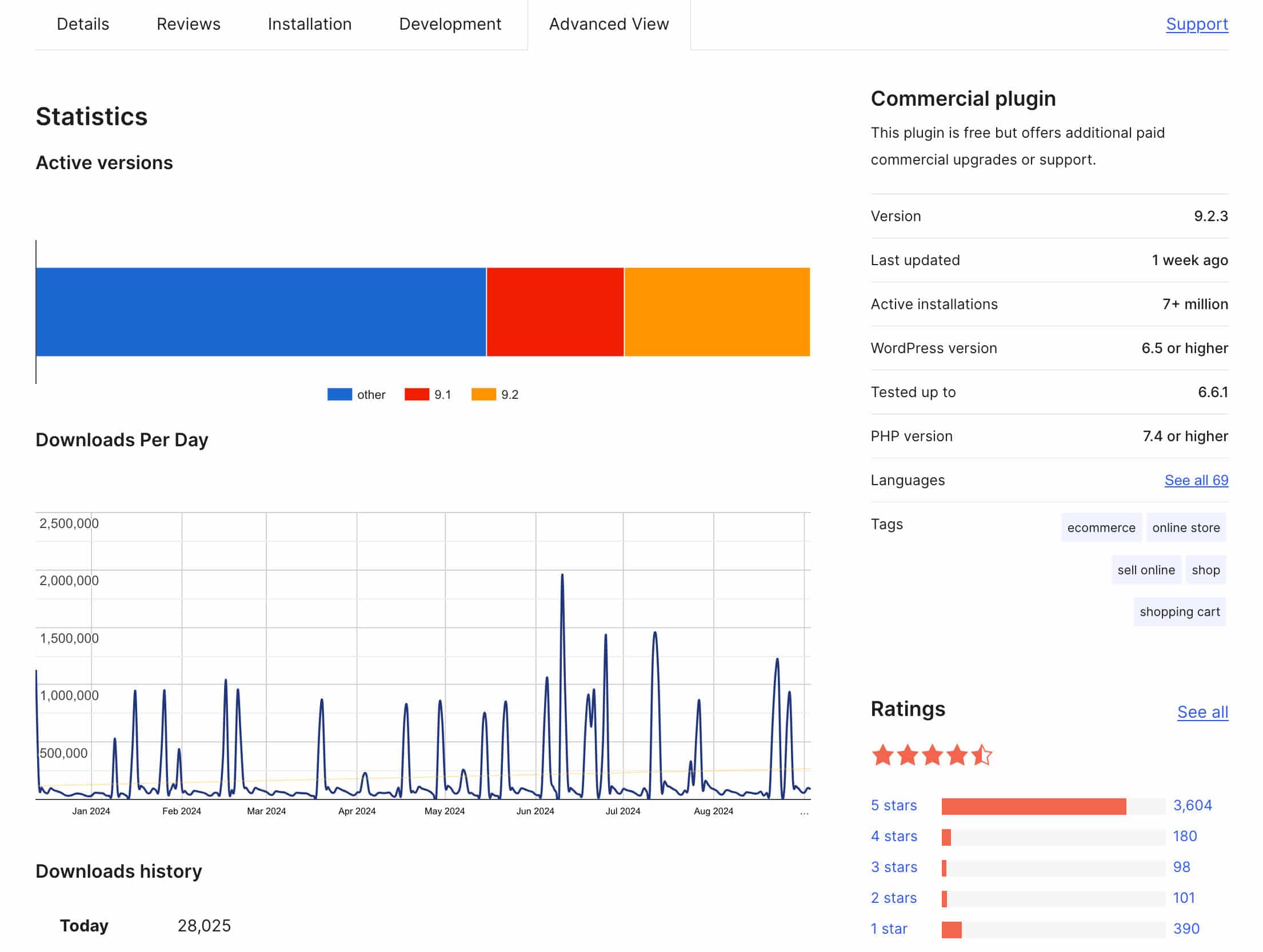
Always test a plugin in a staging environment before using it in production. This prevents compatibility issues with other plugins or the WordPress core itself.
Always back up your site before installing the plugin in production.
Do not install unnecessary plugins or plugins providing redundant features. Unnecessary plugins could potentially create unnecessary security flaws, conflict with other plugins, or reduce site performance.
Check if there are any known vulnerabilities associated with the plugin. Use security services such as the WordPress Vulnerability Database or WPScan.
However, security vulnerabilities can also be detected in popular plugins that receive regular updates. Plugins like WooCommerce and Easy Digital Downloads are no exception.
So, how can a web host help with plugin and theme vulnerabilities?
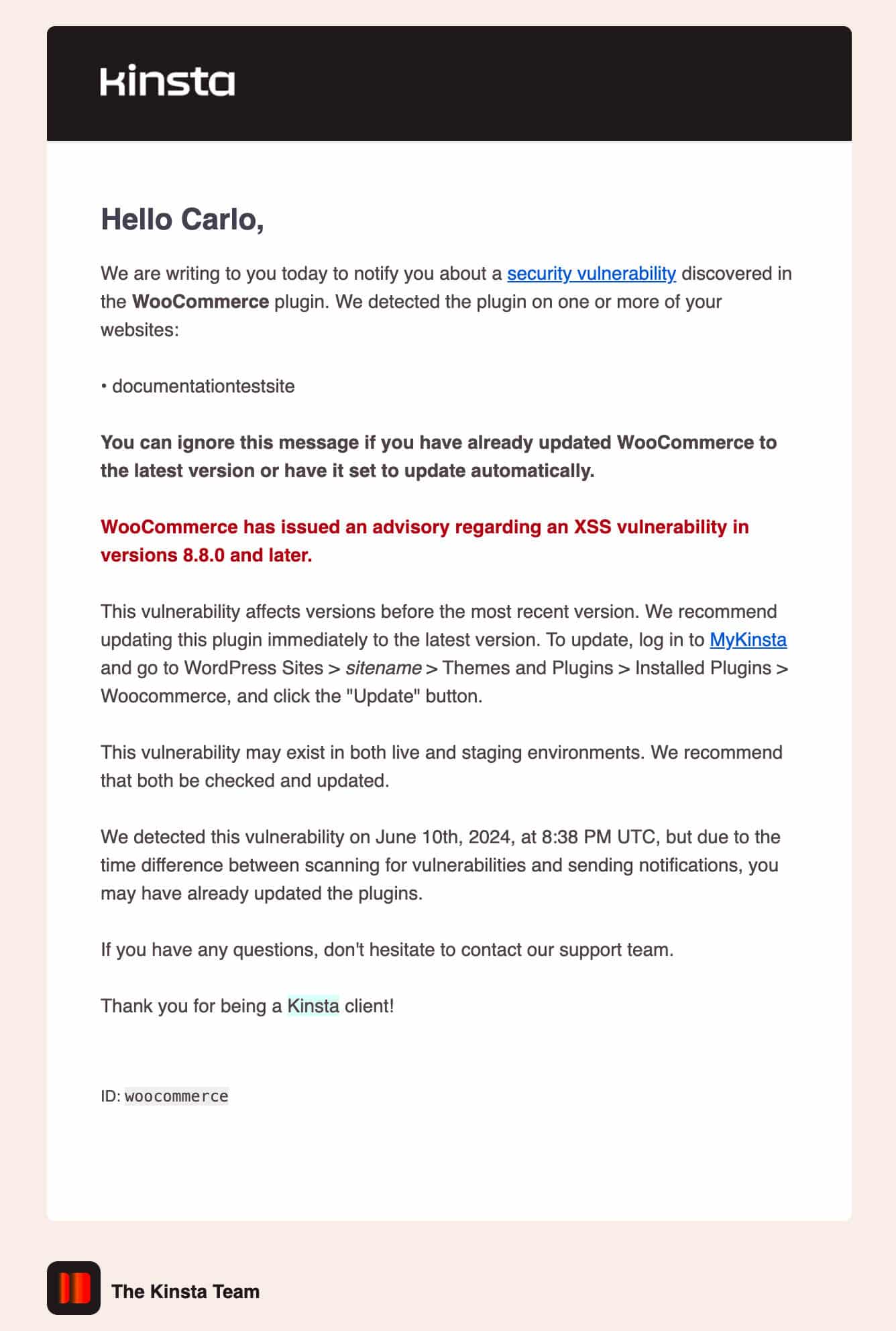
Kinsta security alerts
Whenever a security vulnerability is detected on one of your sites, whether it’s a core, plugin, or theme flaw, you immediately receive a notification in MyKinsta and an email notifying you about the issue and suggesting steps to fix it.
This feature is highly valued by our customers because it allows them to take quick action on vulnerabilities detected on their sites. If you are a Kinsta client, sooner or later, you will most likely receive an email like this:
WordPress-specific threats and how to prevent them
In the first section of this article, we have listed some of the major security threats that affect the generality of e-commerce websites. Some of these threats are particularly serious for WordPress/WooCommerce sites.
Although WordPress is open-source software, it is worth pointing out that hackers do not breach WordPress websites because of inherent vulnerabilities in the CMS but rather because of vulnerabilities that could have been predicted and fixed prior to any incident.
Failure to update the core, plugins, and theme can make your e-commerce website vulnerable, the same way as using weak passwords and not having a strict site access policy.
Here is a quick list of threats and best practices to prevent them that can help you keep your website secure:
For a more comprehensive list of actions you can take to secure WordPress websites, check our WordPress Security Guide and Site Security Cheat Sheet.
More Kinsta features for your e-commerce website security
At Kinsta, our mission is to provide the fastest and most secure WordPress hosting environment in the world. We are always looking for new ways to ensure that your e-commerce websites can offer the best shopping experience to your users and clients. Here are some of Kinsta’s services and features specifically aimed at securing your WordPress/WooCommerce website.
Uptime checks
If your website does not load or its response time is slow, how can you be sure that it is down for everyone or just you?
The short answer is that you need to check if your website is down. You can do it yourself following these steps or, if your site is hosted on Kinsta, you can rely on Kinsta uptime checks.
Kinsta scans your website every 3 minutes. It’s 480 checks every day.
If your site is down, our engineers start working immediately on the problem. There is a very good chance that the problem will be fixed before you even notice it.
Check Out Our Video Guide On How To Check if a Website Is Down:
Kinsta’s security pledge
Keeping an e-commerce site up-to-date is vital for your business, but it may not be enough. For this reason, scanning your website regularly with malware detection tools, such as Sucuri or WordFence, is always recommended even if you do not suspect to have been infected. Our advice is to scan your e-commerce website at least once a month, but we suggest scanning several times a month anytime you make changes to the site structure and install new plugins. If you don’t know where to start, here is a security checklist for your website.
But sometimes, despite all your efforts, it may happen that your site gets infected. What to do then?
Kinsta customers do not have to worry about this because Kinsta provides a free hack fix guarantee for all our clients regardless of their plan. If your WordPress site is hacked while hosted at Kinsta, we’ll work with you for free to try and undo the damage.
Our security pledge includes:
- An inspection of the site and a deep scan of the site’s files to identify malware.
- Repair of the WordPress core by installing a clean copy of the core files.
- Identification and removal of infected plugins and themes.
Check our docs for a more detailed overview of Kinsta’s security pledge.
IP blocking
Sometimes, it may be necessary to block an IP address or range of IPs to prevent malicious behavior from bots, spammers, or other actors. Generally, you can block IP addresses from the server configuration file.
Kinsta users do not have to manually configure their server because Kinsta provides all our customers with a free IP deny tool available in MyKinsta.
To check IPs and the number of requests, log in to MyKinsta and navigate to WordPress Sites > sitename > Analytics > Geo & IP.
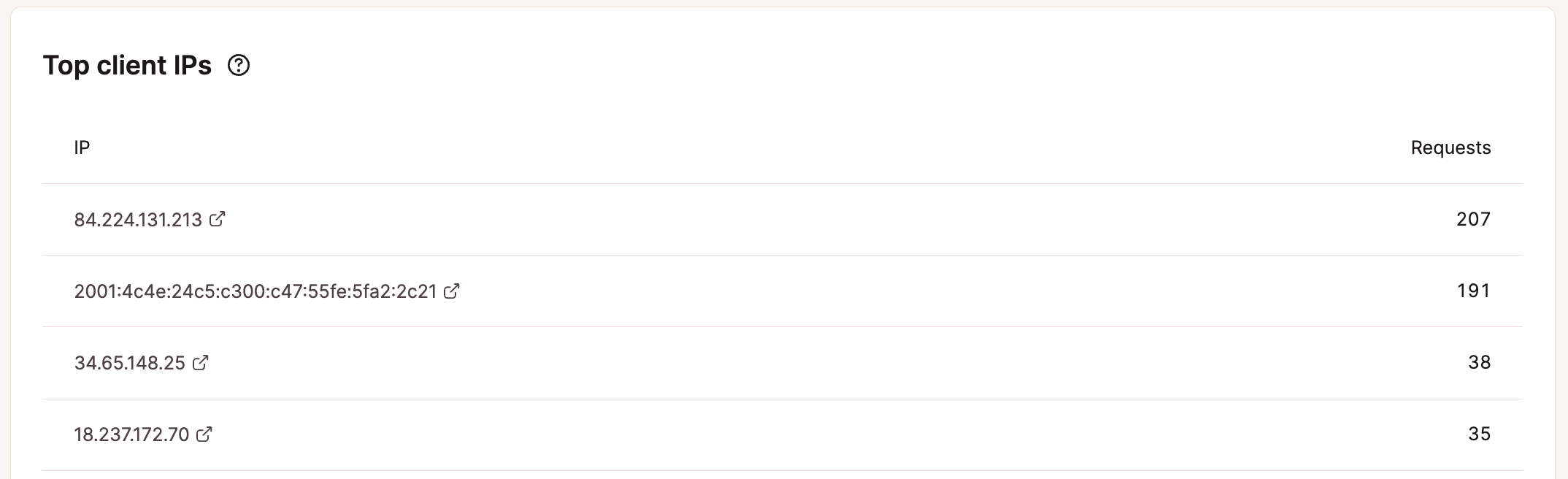
The Top client IPs section shows the list of IP addresses and the number of requests coming from each IP. If you notice an abnormal number of requests from specific IPs, you may want to investigate further through a reputation checker like CleanTalk or Spamhaus to see if the IP address has been identified as a bot, spammer, or other malicious IP address.
If an IP address is identified as malicious, you can block it using the IP Deny tool, available under WordPress Sites > sitename > IP deny.
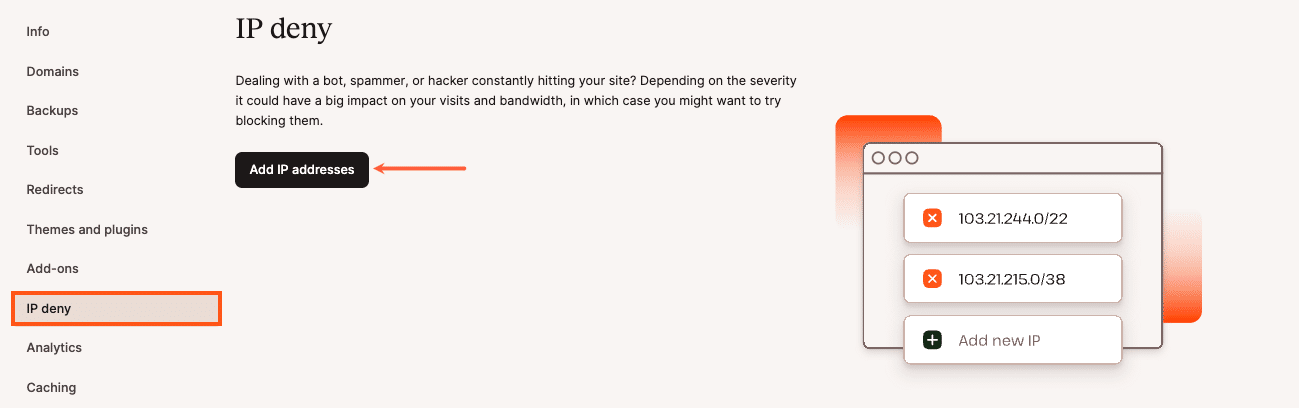
Once you have blocked an IP address, you will see it listed below on the same page.

Kinsta security certifications
Kinsta commitment to ensuring the security of all clients’ sites is verified and certified at different levels.
Kinsta complies with the Security criterion of the System and Organization Controls (SOC 2) compliance framework developed by the American Institute of Certified Public Accountants (AICPA). This standard is used to evaluate a service organization’s adherence to one or more trust services criteria.
The five trust services criteria are:
- Security
- Availability
- Processing integrity
- Confidentiality
- Privacy
But this is not all. Kinsta has achieved ISO 27001, 27017, and 27018 certifications. This achievement reflects adherence to best practices in information security, with additional emphasis on controls safeguarding data in cloud computing environments.
These certifications provide a guarantee of security and stability for all e-commerce website owners who can rely on a hosting service that allows them to devote themselves to their business with peace of mind.
ISO/IEC 27001 is the world’s best-known standard for information security management systems. An ISMS implemented according to this standard “is a tool for risk management, cyber-resilience, and operational excellence.”
Conformity with ISO/IEC 27001 means that an organization or business has put in place a system to manage risks related to the security of data owned or handled by the company and that this system respects all the best practices and principles enshrined in this International Standard.
ISO/IEC 27017:2015 establishes guidelines for information security controls applicable to the provision and use of cloud services. It provides:
- additional implementation guidance for relevant controls specified in ISO/IEC 27002;
- additional controls with implementation guidance that specifically relate to cloud services.
Last, ISO 27018:2019
establishes commonly accepted control objectives, controls, and guidelines for implementing measures to protect Personally Identifiable Information (PII) in line with the privacy principles in ISO/IEC 29100 for the public cloud computing environment.
You can visit Kinsta’s Trust Center for more information on the company’s ongoing compliance efforts.
Summary
There is a lot to be done to secure an e-commerce website. Doing it yourself requires considerable technical skills that may not be available to small businesses and start-ups.
Yet a company owner who wants to launch an online store, accepting the challenge of international markets, should not give up the growth opportunities that e-commerce has to offer. This is where enterprise-level managed WordPress and WooCommerce hosting can help.
As a premium managed WordPress and WooCommerce web hosting service, Kinsta provides a fast and secure cloud hosting for any e-commerce website. With Kinsta, you can launch an online store without worrying about all the technical intricacies, leaving behind an e-commerce website.
Our features include automatic daily backups, a dedicated firewall powered by Cloudflare, real-time monitoring for threats and vulnerabilities, free SSL certificates for encrypted transactions, DDoS protection to guard against malicious traffic, and many more features to protect your e-commerce website.
With all these proactive security measures, Kinsta locks your e-commerce website, minimizing the risk of data breaches and downtime.
Now it’s your turn. What are the risks and vulnerabilities you deal with every day? Does your hosting service provide your e-commerce site with adequate protection against malicious agents? Share your experience in the comments below.

