Sometimes the difference between security and compromise comes down to a single click – and a healthy dose of suspicion. And it’s because scammers are getting increasingly sophisticated with their phishing attempts. It’s to the point where even following standard security best practices isn’t enough to protect you. Case in point: last week’s near-successful phishing attack on Zach Latta.
If you don’t know who Zach is, you’re not alone. I didn’t know who he was either until just last week. After learning more about him, I’d say he’s less famous than he probably should be. His backstory is the stuff of legend.
At the age of 16, he tested out of high school to become a lead backend developer at Yo, earning a Silicon Valley engineer’s salary while most of his peers were still wrestling with algebra. By 2015, he’d caught the attention of Peter Thiel, receiving a $100,000 fellowship to skip college and pursue his vision: Hack Club, a nonprofit that would grow to reach schools across 16 U.S. states and six countries. 1
Why does any of that matter?
It matters because someone with this kind of technical background doesn’t fall for typical phishing scams. So when he posted a detailed breakdown to GitHub last week 2 about “the most sophisticated phishing attack” he had ever seen and how he nearly fell victim to it, it revealed just how convincing modern scams have become.
A call from “Google” ☎️
The caller ID showed a legitimate-looking number.
On the other end, a professional woman who identified herself as “Chloe” spoke with the practiced tone of a Google support representative. Her American accent was flawless and the connection was crystal clear.
She informed Latta that someone had gained access to his account from Frankfurt, Germany. When he said he hadn’t logged in from there recently, she dove into action. It was a classic social engineering tactic – create urgency around a security threat, then offer help.
Building the perfect trap 🪤
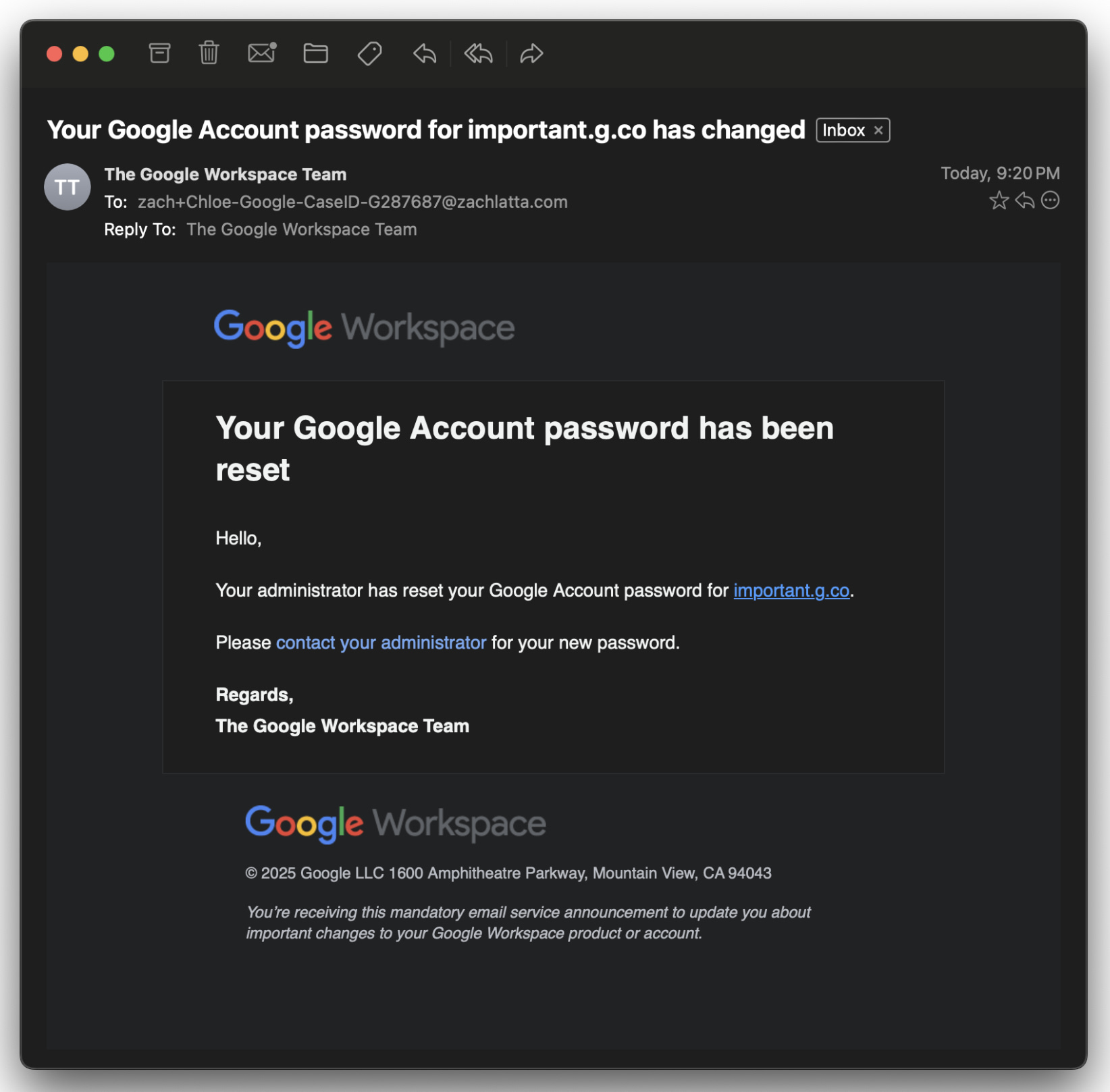
Most phishing attempts fall apart under basic scrutiny. This one was different. When Latta asked the scammer for verification by sending him an email from a Google email address to prove that it was really Google calling, she was ready for it. With no hesitation, she fulfilled his request and emailed him from “important.g.co” – a domain that looked official enough to pass inspection. After all, g.co is Google’s own URL shortener. 3
The attackers had thought of everything. The email headers were perfect. The formatting matched Google’s style exactly. Even the small details about Google Workspace were spot-on.
Gut instinct and a 2FA misstep
But something felt off. When Latta checked his Google Workspace logs, he couldn’t find any suspicious login attempts.
“Chloe” had a ready explanation. She stated that cache delays might be hiding the suspicious activity and followed up with detailed instructions for checking specific log locations. This helped her maintain the temporary facade of technical expertise.
Enter “the manager”
As Latta was checking the logs, the call dropped mid-sentence. Within 30 seconds, he received another call – this time from “Solomon,” who introduced himself as Chloe’s manager. He’d heard about the trouble with the admin logs, he said, and wanted to help personally.
He suggested to Latta that perhaps his Gmail account was compromised through an adblocker Chrome Extension that hijacked his login credentials.
As their conversation continued, Latta grew more suspicious. When he asked Solomon to show him where on Google.com he could find the support phone number he was being called from, Solomon directed him to a page where the number appeared – but only under “Google Assistant.”
What increased Latta’s feeling that something phishy was going on, was that when he asked if he could call the number back – something “Chloe” previously told him was fine – Solomon said no.
Still, he decided to continue playing along.
“Sure, let’s reset the account,” he told Solomon.
In response he was told to open Gmail on his phone and check for the code that Solomon had sent him. By tapping it, it would ensure he would be logged out of all his devices, including the “Frankfurt computer.”
“It should pop up on your screen and say ’84,’” he said confidently. Sure enough, 84 was one of three codes displayed.
This was the moment everything clicked – legitimate two-factor authentication codes are randomly generated and sent to users. No Google employee – or anyone other than the person holding the phone to which the code was sent to – could possibly know it.
Solomon had just revealed his hand. He was trying to trick Latta into approving a malicious account access request.
Recording the ruse
After the “84” code revelation exposed the scam, Latta started recording the call. His iPhone announced this fact to Solomon – a detail that likely rattled the scammer.
Still committed to the charade, Solomon tried one last credibility play: he directed Latta to check his LinkedIn profile as proof he worked at Google. But by now, the “jig was up.”
When Latta pressed him with questions about how they’d pulled off the attack, Solomon sent one final, obviously fraudulent two-factor code before abruptly ending the call.
The (almost) perfect hack and the vulnerability that made it possible 👨🏻💻
What made this attack particularly unnerving wasn’t just its polish – it’s how it twisted standard security advice against itself. “The thing that’s crazy,” Latta wrote, “is that if I followed the two ‘best practices’ of verifying the phone number and getting them to send an email from a legit domain, I would have been compromised.”
After investigating further, Latta and members of Hack Club discovered something troubling: a potential vulnerability in Google Workspace that allows for the creation of new workspaces with any g.co subdomain, bypassing the usual domain ownership checks. The attackers were able to send him an email that appeared legitimate because, in a way, it was.
The entire attack chain demonstrated remarkable precision:
- A spoofed phone number listed on Google’s own support pages.
- Real-time social engineering adapted to each question.
- Exploitation of Google’s own domain verification system.
- Perfect email forgery using a legitimate subdomain.
“Literally one button press from being completely pwned,” Latta reflected. “And I’m pretty technical!”
Looking ahead 🔮
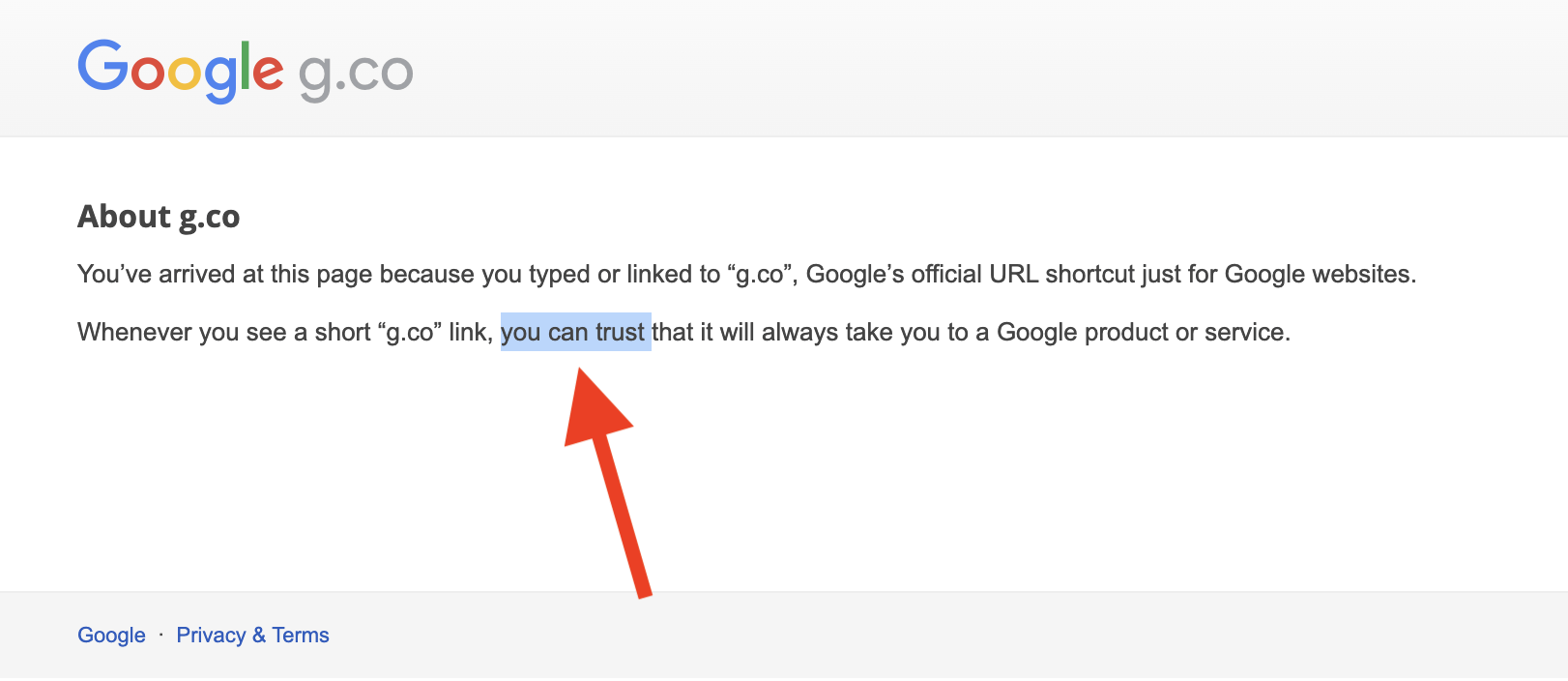
For Google this incident highlights a critical weakness in their g.co official URL shortener. The ability to create subdomains without proper ownership checks is a serious security gap that needs patching.
It also underscores the rapid advancements that scammers have made in their quest to come across as legititmate. Latta, with years of programming experience and security awareness, still came within a hair’s width of compromise.
For security professionals and everyday users alike, it raises uncomfortable questions:
When trusted systems become attack vectors, how do we define “best practices”?
And perhaps more urgently, if a technical expert came this close to compromise, what hope do regular users have?
The answer might lie in Latta’s instincts. Despite multiple verification checks passing, something felt wrong. Sometimes, that gut feeling is your last line of defense. Stay vigilant out there folks!
Have you experienced any recent phishing or hacking attempts? What made you realize you were in the process of an attempted scam? Let’s trade war stories in the comments and see who’s got the most interesting one.
Journalistic credit goes to The Register for being the first online publication to break this story (to my knowledge, anyway).
…
Don’t forget to join our crash course on speeding up your WordPress site. Learn more below:
Or start the conversation in our Facebook group for WordPress professionals. Find answers, share tips, and get help from other WordPress experts. Join now (it’s free)!

